Remote Access Trojan Definition
What Is a RAT Virus?
A remote access trojan (RAT), also called creepware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim.
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT scam via social engineering tactics, or even through temporary physical access of the desired machine.
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control, it is able to do almost everything on the victim machine.
- Get access to confidential info including usernames, passwords, social security numbers, and credit card accounts.
- Monitor web browsers and other computer apps to get search history, emails, chat logs, etc.
- Hijack the system webcam and record videos.
- Monitor user activity by keystroke loggers or spyware.
- Take screenshots on the target PC.
- View, copy, download, edit, or even delete files.
- Format hard disk drives to wipe data.
- Change computer settings.
- Distribute malware and viruses.
Remote Access Trojan Examples
Since spam RAT comes into being, there have existing lots of types of it.
1. Back Orifice
Back Orifice (BO) rootkit is one of the best-known examples of a RAT. It was made by a hacker group named the Cult of the Dead Cow (cDc) to show the security deficiencies of Microsoft’s Windows 9X series of operating systems (OS). The name of this RAT exploit is a play on words on Microsoft BackOffice Server software that can control multiple machines at the same time relying on imaging.
Back Orifice is a computer program developed for remote system administration. It allows a person to control a PC from a remote location. The program debuted at DEF CON 6 on August 1st, 1998. It was created by Sir Dystic, a member of cDc.
Though Back Orifice has legitimate purposes, its features make it a good choice for malicious usage. For this or other reasons, the antivirus industry immediately sorts the tool as malware and appended it to their quarantine lists.
Back Orifice has 2 sequel variants, Back Orifice 2000 released in 1999 and Deep Back Orifice by French Canadian hacking organization QHA.
2. Sakula
Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012. It was used in targeted intrusions throughout 2015. Sakula enables an adversary to run interactive commands and download and execute additional components.
3. Sub7
Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. Its name was derived by spelling NetBus backward (“suBteN”) and swapping “ten” with “seven”.
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1.
Sub7 has not been maintained since 2014.
4. PoisonIvy
PoisonIvy RAT keylogger, also called “Backdoor.Darkmoon”, enables keylogging, screen/video capturing, system administrating, file transferring, password stealing, and traffic relaying. It was designed by a Chinese hacker around 2005 and has been applied in several prominent attacks including the Nitro attacks on chemical companies and the breach of the RSA SecurID authentication tool, both in 2011.
5. DarkComet
DarkComet is created by Jean-Pierre Lesueur, known as DarkCoderSc, an independent programmer and computer security coder from France. Although this RAT application was developed back in 2008, it began to proliferate at the start of 2012.
In August 2018, DarkComet was ceased indefinitely and its downloads are no longer offered on its official website. The reason is due to its usage in the Syrian civil war to monitor activists as well as its author’s fear of being arrested for unnamed reasons.
Besides the above examples, there are many other remote access trojan programs like CyberGate, Optix, ProRat, Shark, Turkojan, and VorteX. The full list of RAT tools is too long to be displayed here and it is still growing.
RAT Virus Symptoms
How to tell if you have a RAT virus? It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself.
Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs. Besides, RAT spyware will manage the use of computer resources and block the warning of low PC performance. Also, RAT hackers usually won’t give themselves away by deleting your files or moving your cursor while you are using your computer.
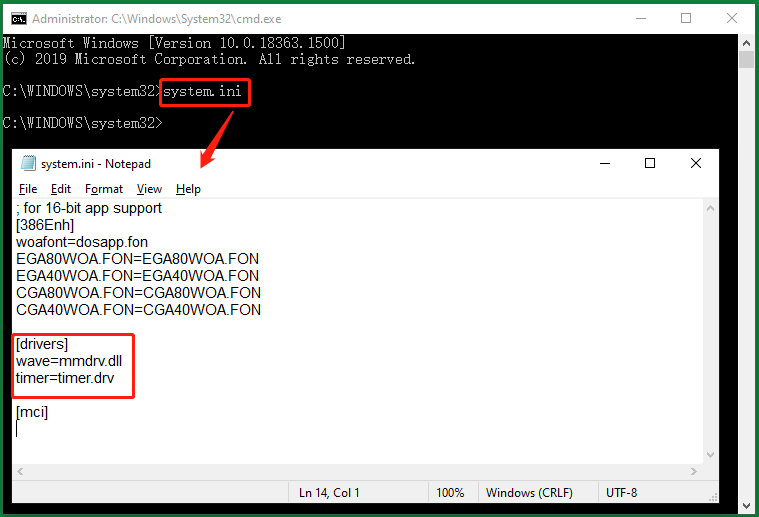
FYI: Use System.ini to Identify RAT Infection
Open the command prompt better as administrator, type “system.ini”, and press Enter. Then, a notepad will pop up showing you a few details of your system. Take a look at the drivers section, if it looks brief as what the below picture shows, you are safe. if there are some other odd characters, there may be some remote devices accessing your system via some of your network ports.
Remote Access Trojan Detection
How to detect remote access trojan? If you can’t decide whether you are using a RAT virus computer or not just by symptoms (there are few symptoms), you need to ask for some external help like relying on antivirus programs. Many common security apps are good RAT virus scanners and RAT detectors.
Top Remote Access Trojan Removal Tools
- Avast
- AVG
- Avira
- Bitdefender
- Kaspersky
- Malwarebytes
- McAfee
- Microsoft Windows Defender
- Norton
- PC Matic
- Sophos
- Trend Micro
FIY: Find RAT with CMD and Task Manager
You can try to figure out suspicious items together with Task Manager and CMD. Type “netstat -ano” in your command prompt and find out the PID of established programs that has a foreign IP address and appears REPEATEDLY. Then, look up the same PID in the Details tab in Task Manager to find out the target program. Yet, it doesn’t mean the target program is a RAT for sure, just a suspicious program. To confirm the founded program is RAT malware, further identification is needed.
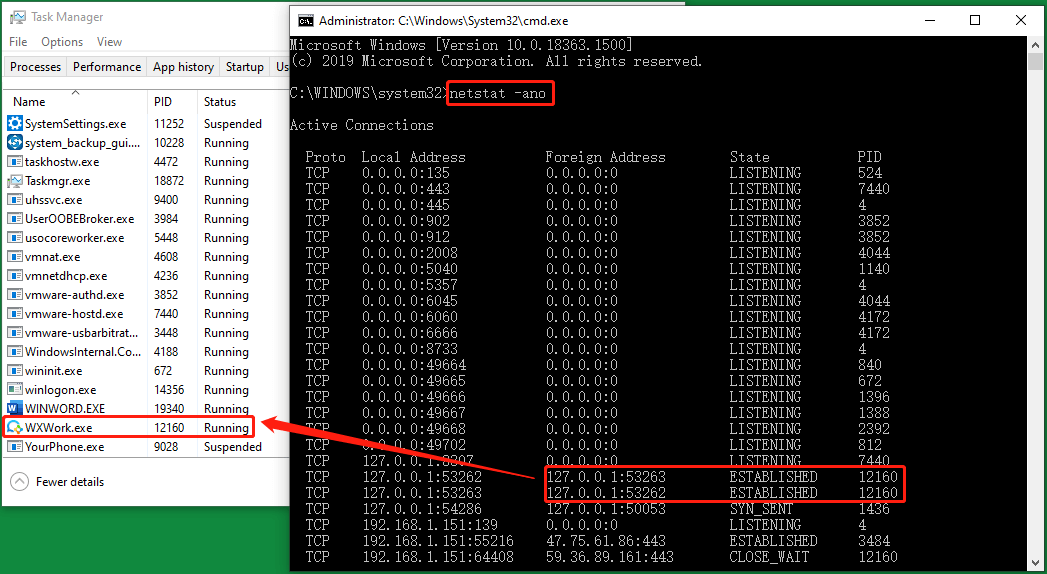
You can also use the suspicious foreign IP address to find out its registered location online. Many websites that can help you do that like https://whatismyipaddress.com/. If the location has no connection to you completely, not the location of your friends, company, relatives, school, VPN, etc., it probably is a hacker location.
Remote Access Trojan Removal
How to remove a remote access trojan? Or, how to get rid of a RAT virus?
Stage 1
If you can locate specific malicious files or programs, just clear them out of your computer or at least end their processes. You can do this in Task Manager or Windows MSConfig utility.
Type “misconfig” in Windows Run and press Enter or click OK to trigger the MSConfig window. There, switch to the Services tab, find the target services and disable them.
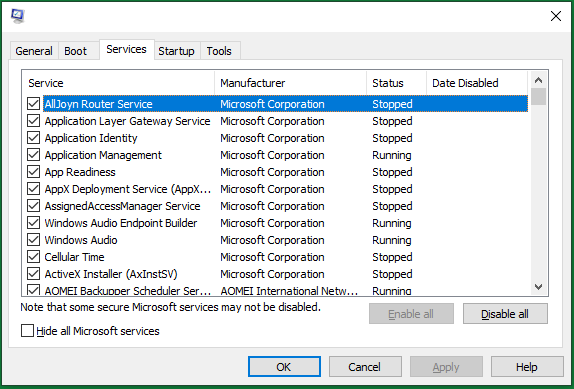
Just restart your machine after you uninstalling or blocking some programs or services.
Stage 2
Install and run a RAT remover like Malwarebytes Anti-Malware and Anti-Exploit to remove associated files and registry modifications.
Stage 3
Use checking tools, such as Autorun.exe, to check suspicious files and programs that starting up when windows boot up.
Stage 4
Check network connections going out or coming into your system that should not exist. Or, just directly cut off your Internet connection.
How to Protect Yourself from RAT Cyber Attack?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
#1 Avoid Downloading from Untrusted Sources
First of all, the most effective and easiest prevention is never to download files from unsecured sources. Instead, always get what you want from trusted, authorized, official, and safe locations such as official websites, authorized stores, and well-known resources.
#2 Keep Firewalls and Antivirus up to Date
No matter which firewall or antimalware program you have, or even if you have more than one of them, just keep those security services all up to date. The newest versions always adopt the latest security technologies and are specially designed for the current popular threats.
The above-mentioned Malwarebytes and other antiviruses can also prevent the initial infection vector from allowing the system to be compromised.
#3 Change Your Usernames and Passwords Regularly
It is a good habit to change your various accounts regularly to fight against account theft, especially for passwords. Besides, you are recommended to take advantage of the various kinds of security features provided by the service vendors to secure your accounts like two-factor authentication (2FA).
#4 Upgrade Your Legal Programs
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
#5 Upgrade Computer System
Of course, don’t forget to patch your OS with the latest updates. Usually, the system updates include patches and solutions for recent vulnerabilities, exploits, errors, bugs, backdoors, and so on. To upgrade the operating system to safeguard your whole machine!
Back up Files Against RAT Software Virus
It is often the case that cyber RATs go undetected for years on workstations or networks. This indicates that antivirus programs are not infallible and should not be treated as the be-all and end-all for RAT protection.
Then, what else can you do to protect your computer files from being edited, deleted, or destroyed? Luckily, you can still regain your data after malware RAT attacks if you have a backup copy of it. Yet, you have to make the copy before you lost the original files with a reliable and RAT-free tool such as MiniTool ShadowMaker, which is a professional and powerful backup program for Windows computers.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 1. Download MiniTool ShadowMaker from its official website or the above-authorized link button.
Step 2. Install and launch the tool on your PC.
Step 3. If you get its Trial version, you will be prompted to buy its paid editions. If you don’t want to pay, just click the Keep Trial option in the upper right to enjoy its trial functions, which are the same as the formal features only with a time limit.
Step 4. When you enter its main interface, click the Backup tab on the top menu.
Step 5. In the Backup tab, specify the Source files you plan to copy and the Destination location you’d like to save the backup image.
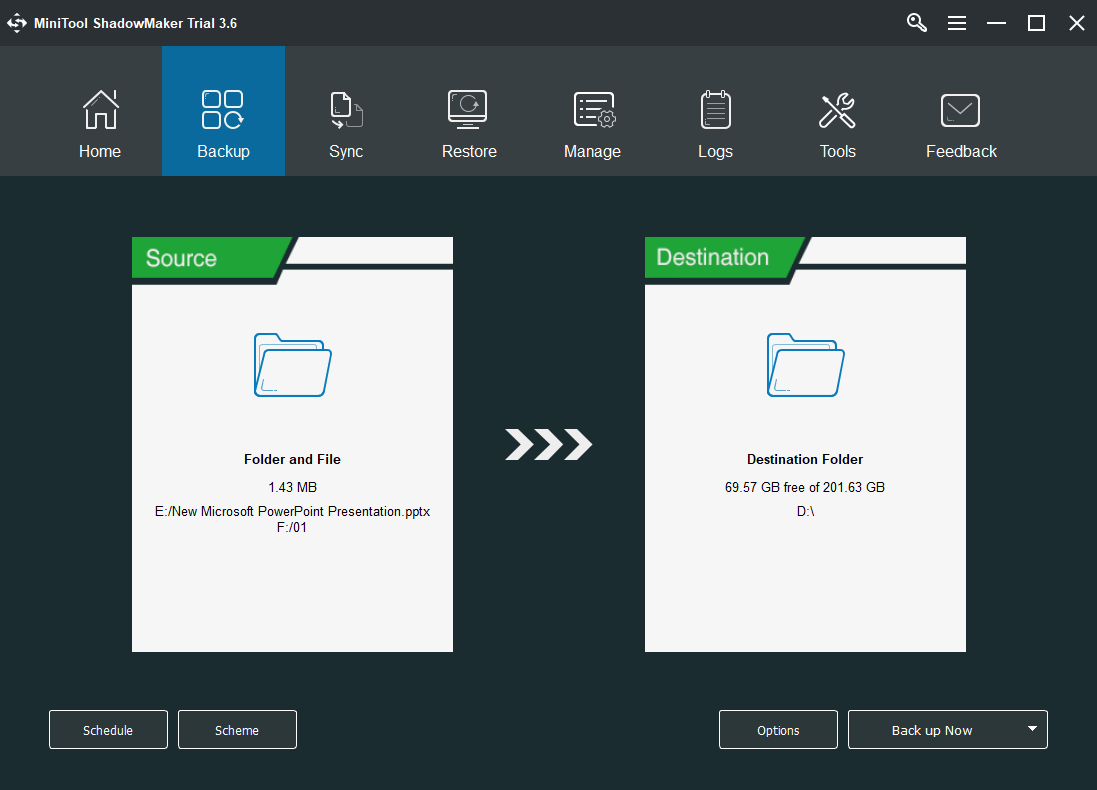
Step 6. Click the Back up Now button in the lower right to carry out the process.
The rest is to wait for the success of the task. You can set up a schedule to automatically back up those files daily, weekly, monthly, or when the system logs on/off in the above Step 5 before the process startup or in the Manage tab after the process. Also, you can decide which kind of backups to execute, full, incremental, or differential, as well as how many versions of the backup image to keep in case running out of storage space.



User Comments :