This post will introduce you a support protocol in the Internet protocol suite – ICMP. What is this ICMP protocol? Well, you can get the details from this post.
ICMP Definition
What is ICMP? The ICMP (Internet Control Message Protocol) is an error-reporting protocol used for network devices like routers. It will generate error messages to the original IP address when IP packets are prevented due to network issues.
For instance, it will send you a message when a requested service is not available (DNS server unavailable) or a router could not be reached, etc. Different from transport protocols like TCP and UDP, ICMP usually is not used to exchange data between systems and utilized by end-user network applications (except some diagnostic tools such as ping and traceroute).
How does ICMP work? Where is ICMP protocol applied? You can get the detailed information from this post of MiniTool.
You may also be interested in this: The Details of ISCSI (Internet Small Computer System Interface)
The Working Theory of ICMP
Before understanding the working theory of ICMP, you should have a look for its structure. While this is directly linked to the IP header that is marked by the protocol number 1 or 58 (ICMPv6) in the field of protocol. The header data area of ICMP is limited and has a form as shown in below.
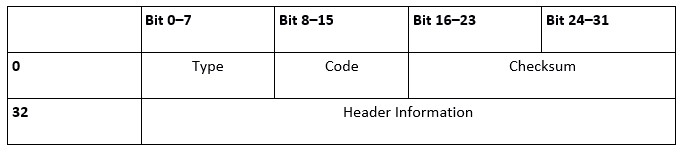
As the table shows, the first 8-bit decides the type of notification the ICMP packet. The information can be specified further with the below code field, which also has a length of 8-bit. As for ICMP checksum, it follows the information about the message type. Besides, it can ensure the accuracy of the notification.
Highly recommended: Packet Loss [The Definition, Possible Causes and Fixes]
This operates in a way that is the same with the checksum of other standard protocols like IP, UDP, and TCP do. The ICMP files are built and structured differently based on the respective type and the triggering instance.
The IP header usually includes a list of the first 64 bits of the data packet, which manage the error message and the status query. When the ICMP tunneling occurs, this field is used to send useful data under firewall’s radars or set up an encrypted communication channel between computer PCs.
You may like this: What Is Asynchronous Transfer Mode (ATM) & How Does It Work
The Application of ICMP
When talking about ICMP, it is inevitable to discuss its application. What is ICMP used for? According to investigation, ICMP protocol has 2 uses. The first and foremost one is error reporting. The send one is network diagnostics. Now, let’s explain them one by one.
Error reporting
ICMP is vital in the communication of IP networks. It is often used in routers. When 2 devices connect over Internet, ICMP will produce error message and send it to the original device as long as any of data does not reach the expected destination.
Therefore, ICMP is very useful for users. Because of this feature, ICMP is widely used.
Network Diagnostics
Another application of ICMP is to perform network diagnostics. The ICMP is commonly utilized in traceroute and ping. The traceroute is often used to show the routing path between the two Internet devices. The routing path in fact is the physical path of connected routers – a request must pass through it before the router arrives at the destination.
The trip between one router and another is famous as a “hop”. Here, you need to know that a traceroute also tells the time that is required for each hop. This can help you determine the sources of network delay.
How about ping? Actually, the ping utility is a simplified version of traceroute, which can test the speed of the connection between two devices. In addition, it will tell you the time it takes to reach the destination and return to the sender’s device. Even though ping will not offer data about routing or hops, it is still useful for measuring the latency between two devices.
In the practical life, the ICMP echo-request and echo-reply messages are often used for performing a ping. However, network attackers can make use of this process and create disruptions like ICMP Flood Attack and Ping of Death.
Top recommendation: How to Fix High Ping? Here Are Some Methods for You
The Bottom Line
To sum up, this post talks about the ICMP definition, and ICMP working theory and main applications. After reading this post, you will have an overall understanding of ICMP protocol. Here comes the end of this post.
User Comments :