First of all, whether White Hat or Black Hat, they are both used to classify hackers, which is inspired by early Western movies, where the heroes could be identified by the white hats they wore and the villains by their black hats.
Therefore, you can easily tell that not all hackers are regarded as malicious enemies. The main category for hackers is classified into three types – White Hat hackers, Black Hat Hackers, and Grey Hat hackers, from which you can also discriminate by their motives – Ethical hackers, Malicious hackers, and not malicious but not always ethical hackers.
Therefore, to figure out the difference between White Hat and Black Hat, you can start with their definitions and work principles.
What Is White Hat?
The cyber term – White Hat hacker refers to a programmer who takes the position of a hacker and attacks his or her own system to check for security vulnerabilities. They do it in the same way that hackers (commonly referred to as Black Hat hackers) use to disrupt attacks, but they do it to maintain security.
They usually have highly-skilled expertise and professional knowledge to find vulnerabilities in a system but different from a Black Hat hacker, they are authorized or certified to hack organizational networks and computer systems so that weaknesses in the security systems can be disclosed and they are able to find their way safeguarding them against external attacks and data breaches.
Many enterprises and governments are dying for those professionals to ramp up their defense walls. Those White Hat hackers often get highly paid and they can also work for personal interest.
What Is Black Hat?
Black Hat hackers often use their skills to steal other people’s resources on the network or crack software charged for profit. Although in their view it is because of the technology, this behavior often disrupts the order of the whole market or leaks the privacy of others.
They can break into systems, steal information, manipulate data, and compromise security and their attacks can range from simple Malware spreading to complex vulnerability exploitation and data theft.
White Hat vs Black Hat
White Hat vs Black Hat Intentions
Their motives are the greatest difference between White Hat hackers and Black Hat hackers.
As we have mentioned before, to better identify your enemies and partners, hackers have been divided into ethical hackers and malicious hackers, which means some of them do system attacks for good and valid reasons but some for financial gain, political interest, or malicious revenge.
Otherwise, even though they use the same channels to apply an attack, as long as the action gets approved by the attacked, the attacker can seem legal and ethical.
Ethical hacking is accepted by social recognition, known as the “defenders of information security”, the “guardians” of the Internet world, and the indispensable backbone of the “Internet +” context; Black Hat hacking belongs to the illegal event for its disturbing social rules.
White Hat vs Black Hat Techniques
Although White Hat hackers and Black Hat hackers both aim to attack systems and find weaknesses in the security system, the techniques and methods are different.
White Hat Hacking
1. Social engineering
Social engineering is about tricking and manipulating victims into doing something they should not, such as making wire transfers, sharing login credentials, and so on.
2. Penetration testing
Penetration testing aims to uncover vulnerabilities and weaknesses in an organization’s defenses and endpoints so they can be rectified.
3. Reconnaissance and research
This involves doing research on the organization to find vulnerabilities in the physical and IT infrastructure. The goal is to obtain enough information to identify ways to legally bypass security controls and mechanisms without breaking or destroying anything.
4. Programming
White Hat hackers create honeypots as decoys that lure cybercriminals to distract them and gain valuable information about their attackers.
5. Use a variety of digital and physical tools
They can install bots and other malware and gain access to the network or servers.
Black Hat Hacking
Black hat hackers’ techniques are constantly evolving but the main attack methods won’t change too much. Here is a list of hacking techniques you may encounter.
1. Phishing attacks
Phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity.
2. DDoS attacks
A DDoS attack is an attempt to crash an online service by flooding it with synthetically generated traffic. To learn more details about DDoS attacks, please refer to this article: What Is DDoS Attack? How to Prevent DDoS Attack.
3. Trojan virus
A Trojan virus is a type of malware that conceals its true content, disguised as free software, videos, or music, or appears as legitimate advertisements, to fool a user into thinking it’s a harmless file.
4. Some of the other popular techniques include:
- Logic bombs
- Keylogging
- Ransomware
- Fake W.A.P.
- Brute force
- Switch attacks
- Cookie theft
- Bait attack
White Hat vs Black Hat Work Principles
Apart from their working motives and techniques, you can tell them apart by their working principles.
White Hat hackers
There are five stages for White Hat hackers:
Stage 1: Footprinting
Footprinting is a technique for gathering as much information as possible about a targeted computer system, infrastructure, and network to identify opportunities to penetrate them. It is one of the most effective methods for identifying vulnerabilities.
Stage 2: Scanning
After gathering the needed information, hackers will start accessing the network and skimming for information, such as user accounts, credentials, and IP addresses.
Stage 3: Gaining access
This phase is where an attacker breaks into the system/network using various tools or methods. After entering into a system, he has to increase his privilege to the administrator level so he can install an application he needs or modify data or hide data.
Stage 4: Maintaining access
It is the process where the hacker has already gained access to a system. After gaining access, the hacker installs some backdoors in order to enter into the system when he needs access to this owned system in the future.
Stage 5: Analysis
Vulnerability analysis is a procedure to check all the vulnerabilities in the systems, computers, and other ecosystem tools. The vulnerability analysis helps in analyzing, recognizing, and ranking the vulnerabilities.
It helps with the identification and assessment of threat details, enabling us to keep a resolution to protect them from hackers.
Black Hat hackers
- Create and launch malware and DDoS attacks to disrupt operations and cause general chaos and destruction.
- Create fake social media profiles of people you trust in order to manipulate you into disclosing confidential or banking information.
- Steal user data by penetrating leaky databases.
- Spread malware or defraud people by using phishing attacks.
- Constantly look for vulnerabilities in order to find ways to exploit them for personal gain.
- Install spyware on their targets’ devices to blackmail victims.
How to Protect Yourself from Black Hat Hackers?
Don’t Access Personal or Financial Data with Public Wi-Fi
The biggest threat to free Wi-Fi security is the ability of the hacker to position himself between you and the connection point. So instead of talking directly with the hotspot, you’re sending your information to the hacker, who then relays it on.
Turn off Features You Don’t Need
Apart from your Wi-Fi, any feature that can be a bridge between you and hackers is dangerous, such as GPS, Bluetooth, and some apps. You can just turn them on only when you need them.
Choose Your Apps Wisely
Apps are a common channel to hide malicious codes. To avoid that, you’d better download and install programs from trustworthy websites in case some links will bring you dangerous viruses and attached programs.
Besides, just remember to update your apps regularly and timely remove those unneeded programs.
Use a Password, Lock Code, or Encryption.
- Use a reputable encrypted password manager.
- Make sure your passwords are at least eight characters long, with a mix of upper and lower case, and include numbers or other characters.
- Use the storage encryption feature.
- Set your screen to timeout after five minutes or less.
Back up Your Data in Advance
After studying the difference between White Hat and Black Hat, you have a general picture of what they are and how to tell them apart. However, even though the picture has been shown and a precautionary plan has been disclosed, every ignored detail can let you become a target exposed in front of hackers.
To minimize your loss and prevent system crashes or other severe disasters made by hackers, preparing a backup plan can always be your last resort to recover your lost data. MiniTool ShadowMaker has devoted itself to this field for years and sees greater advances and breakthroughs.
To back up with MiniTool ShadowMaker, you need to download and install the program first and you will get a free trial version for 30 days.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 1: Click Keep trial to enter the program and switch to the Backup tab.
Step 2: Click the Source section and in the pop-up window you can choose backup content including system, disk, partition, folder, and file. By default, the system has been set as the backup source already.
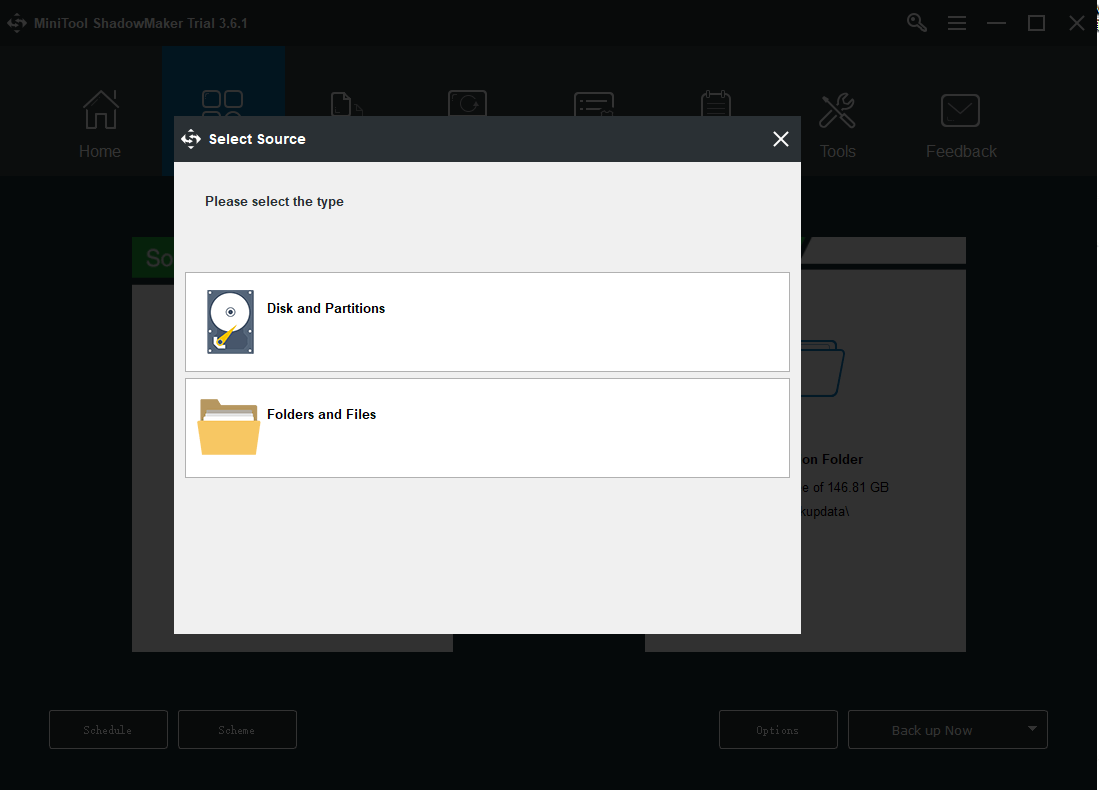
Step 3: Go to the Destination part where you can see four options containing the Administrator account folder, Libraries, Computer, and Shared. Then choose your destination path. And then click OK to save your changes.
Step 4: Click the Back up Now option to start the process immediately or the Back up Later option to delay the backup. The delayed backup task is on the Manage page.
Besides, with MiniTool ShadowMaker, you can sync your files or clone disk. The services you can enjoy are more than backup. One of the useful functions – Universal Restore – can help you resolve the incompatibility issue if you want to restore a system on other computers.
Bottom Line:
In most cases, it is hard to totally prevent all hacking events if you are at high risk of exposing your important and valuable data to the outside which is quite easily found in this Internet-connected world. Anyway, some methods can help you minimize the loss and a backup plan can be your last resort.
If you have encountered any issues when using MiniTool ShadowMaker, you can leave a message in the following comment zone and we will reply as soon as possible. If you need any help when using MiniTool software, you may contact us via [email protected].
White Hat vs Black Hat FAQ
White hats deserve legal respect. But White Hats can also have legal exposure and vulnerability to lawsuits, even when they hack systems with good intent, but do so essentially unsolicited or uninvited within the context of a formal contractual engagement by a principal.
There are three well-known types of hackers in the world of information security: black hats, white hats, and grey hats. These colored hat descriptions were born as hackers tried to differentiate themselves and separate the good hackers from the bad.
The CEH is a vendor-neutral credential, and CEH-certified professionals are in high demand. The median salary of an ethical hacker is slightly above $80,000, according to PayScale, and the top range can reach well over $100,000.
There are several ways to earn money as a black hat. Some of them are hackers for hire; basically online mercenaries. Other ways include stealing credit card information from victims, selling the numbers on the dark web, or using a victim's machine for crypto mining.

User Comments :