In this world where people rely more on the Internet, some malicious events are happening in the cyber world. Criminals are trying everything they can do to exploit people’s privacy and steal data, like DDoS and DoS attacks. Today, this article about DDoS vs DoS on MiniTool Website will introduce their differences.
With more kinds of cyber attacks, people need to know more about them so that specific methods can be designed for target attacks. Therefore, to prevent these two powerful enemies – DDoS attacks and DoS attacks, you must figure out what they are.
What Are DDoS Attacks?
DDoS Attack (Distributed Denial-of-Service Attack) is a cybercrime in which the attacker floods a server with Internet traffic to prevent users from accessing connected online services and sites. Actually, it is much similar to DoS attacks so that many people will mistake these two attacks.
If you want to know more details about DDoS attacks, you can refer to this article: What Is DDoS Attack? How to Prevent DDoS Attack.
What Are DoS Attacks?
A denial of service (DoS) attack is a type of network attack in which an attacker attempts to make a machine or network resource unavailable to its target user by temporarily or indefinitely disrupting the service of hosts connected to the network.
Types of DoS Attacks and DDoS Attacks
Although they share similar purposes of attacking computers, you still can classify them by their different attacking methods. This is one big difference between DoS attacks and DDoS attacks. There are three types of DoS attacks and DoS attacks respectively.
Three Types of DoS Attacks
Teardrop Attack
The teardrop attack exploits the information in the packet’s header in the TCP/IP stack implementation that trusts the IP fragment.
An IP segment contains information indicating which segment of the original packet the segment contains, and some TCP/IP stacks, such as NT before Service Pack4, will crash upon receiving a forged segment with overlapping offsets.
When an IP packet is transmitted over a network, the packet can be divided into smaller pieces. An attacker can implement a Teardrop attack by sending two (or more) packets.
Flooding Attack
SYN flooding attacks exploit TCP’s three-way handshake mechanism. The attacker sends a request to the attacked end by using a forged IP address, and the response packet sent by the attacked end never reaches the destination. In this case, the attacked end consumes resources while waiting for the connection to be closed.
If there are thousands of such connections, the host resources will be exhausted, thus achieving the goal of the attack.
IP Fragmentation Attack
IP fragmentation attack refers to a kind of computer program reorganization vulnerability. It can send the modified network packets, but the receiving network cannot be reorganized. Due to a large number of unassembled packets, the network gets bogged down and uses up all its resources.
Three Types of DDoS Attacks
Volumetric Attacks
Volumetric attacks are conducted by bombarding a server with so much traffic that its bandwidth gets completely exhausted.
In such an attack, a malicious actor sends requests to a DNS server, using the spoofed IP address of the target. The DNS server then sends its response to the target server. When done at scale, the deluge of DNS responses can wreak havoc on the target server.
Protocol Attacks
Protocol DDoS attacks rely on weaknesses in Internet communications protocols. Because many of these protocols are in global use, changing how they work is complicated and very slow to roll out.
For example, Border Gateway Protocol (BGP) hijacking is a great example of a protocol that can become the basis of a DDoS attack.
Web Application-based Attacks
An application attack consists of cyber criminals gaining access to unauthorized areas. Attackers most commonly start with a look at the application layer, hunting for application vulnerabilities written within code.
DDoS vs DoS Attacks
To compare DDoS attacks to DoS attacks, this article will clarify the differences in their important features.
Internet Connection
The key difference between DoS and DDoS attacks is that DDoS uses multiple Internet connections to put the victim’s computer network offline whereas DoS uses a single connection.
Speed of Attack
DDoS is a faster attack compared to a DoS attack. Because DDoS attacks come from multiple locations, they can be deployed much faster than DoS attacks with a single location. The increased speed of the attack makes it more difficult to detect, which means increased damage or even catastrophic results.
Ease of Detection
DoS attacks are easier to trace compared to DDoS attacks. The speed comparison result has told us that DDoS attacks perform faster than DoS, which can make the attack hard to detect.
Besides, since a DoS comes from a single location, it is easier to detect its origin and sever the connection.
Traffic Volume
DDoS attacks allow the attacker to send massive volumes of traffic to the victim network. A DDoS attack employs multiple remote machines (zombies or bots), which means that it can send much larger amounts of traffic from various locations simultaneously, overloading a server rapidly in a manner that eludes detection.
Manner of Execution
In DDoS attacks, the victim PC is loaded from the packet of data sent from Multiple locations; in DoS attacks, the victim PC is loaded from the packet of data sent from a single location.
DDoS attacks coordinate multiple hosts infected with malware (bots) to create a botnet managed by a command and control (C&C) server. In contrast, DoS attacks typically use scripts or tools to execute attacks from a single machine.
Which One Is More Dangerous?
According to the above comparison between DDoS attacks and DoS attacks, it is apparent to see that DDoS attacks exceed in many aspects, which makes DDoS attacks become a tougher issue until now.
DDoS and DoS attacks are both dangerous and any of them can lead to a severe shutdown issue. But DDoS attacks are more dangerous than DoS attacks because the former are launched from distributed systems while the latter is executed from a single system.
If you want to know how to identify if you are undergoing DDoS attacks or DoS attacks. There are some signals you may figure out.
- An unseen slow network performance.
- A denial of service by one of the digital properties.
- An unknown loss of network connectivity to machines on the same network.
- Any sudden downtime or performance issues.
Why Do DoS and DDoS Attacks Occur?
The Seek for Benefits
Most cyber-criminal activities originate from the seek for benefits. On the Internet, there is a special treasure that has a great appeal to criminals – virtual assets. With multiple attacks, some e-commerce websites will crash and what’s more serious is the economic losses.
Besides, people’s privacy is also regarded as a profitable asset. That can be sold to the companies in need, such as shopping platforms or other services businesses.
Ideological Beliefs
For those hackers, what they want is not to benefit but to demonstrate their political support or dissent. They will target politicians, political groups, or other government and non-government organizations because their ideological beliefs differ to shut down a website.
Cyberwarfare
When some people claim their political dissent in such an aggressive way, people with different political support will fight back in the same way, which, therefore, triggers cyber-warfare. Usually, different DDoS attack types are attempted by militants and terrorists for political or military purposes.
Malicious Competitors
For the sake of personal interest, some competitors will take malicious actions to attack their rivals and DDoS attacks are commonly used in commercial wars.
DDoS attacks can make an enterprise’s network down, during which the rivals can steal their customers.
How to Prevent DDoS and DoS Attacks?
Now that you have learned about DoS vs DDoS attacks, you may wonder if there are any available methods used for precaution. To prevent DDoS attacks and DoS attacks, you can do as follows.
- Create multi-layered DDoS protection.
- Apply web application firewalls.
- Know the symptoms of the attack.
- Practice continuous monitoring of network traffic.
- Limit network broadcasting.
- Have a server redundancy.
Apart from that, it is worthwhile stressing the importance of backup. Whatever DDoS attacks or DoS attacks, they can lead to slow Internet performance, website shutdown, system crashes, etc. Only if you have prepared a system backup in other external disks, the system restoration can perform soon.
In this way, MniTool ShadowMaker can fulfill your demands and other available features are set to improve your backup experience. You can make a scheduled backup (Daily, Weekly, Monthly, On Event) and backup scheme (full backup, incremental backup, differential backup) for your convenience.
Go to download and install this program and you can enjoy a trial version for 30-days free.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 1: Open MiniTool ShadowMaker and click Keep trial to enter the program.
Step 2: Go to the Backup tab and the System has been selected as the source. If you want to change to other backup targets – the disk, partition, folder, and file – or other backup destinations – the Administrator account folder, Libraries, Computer, and Shared, you can click on the Source or Destination section and re-select them.
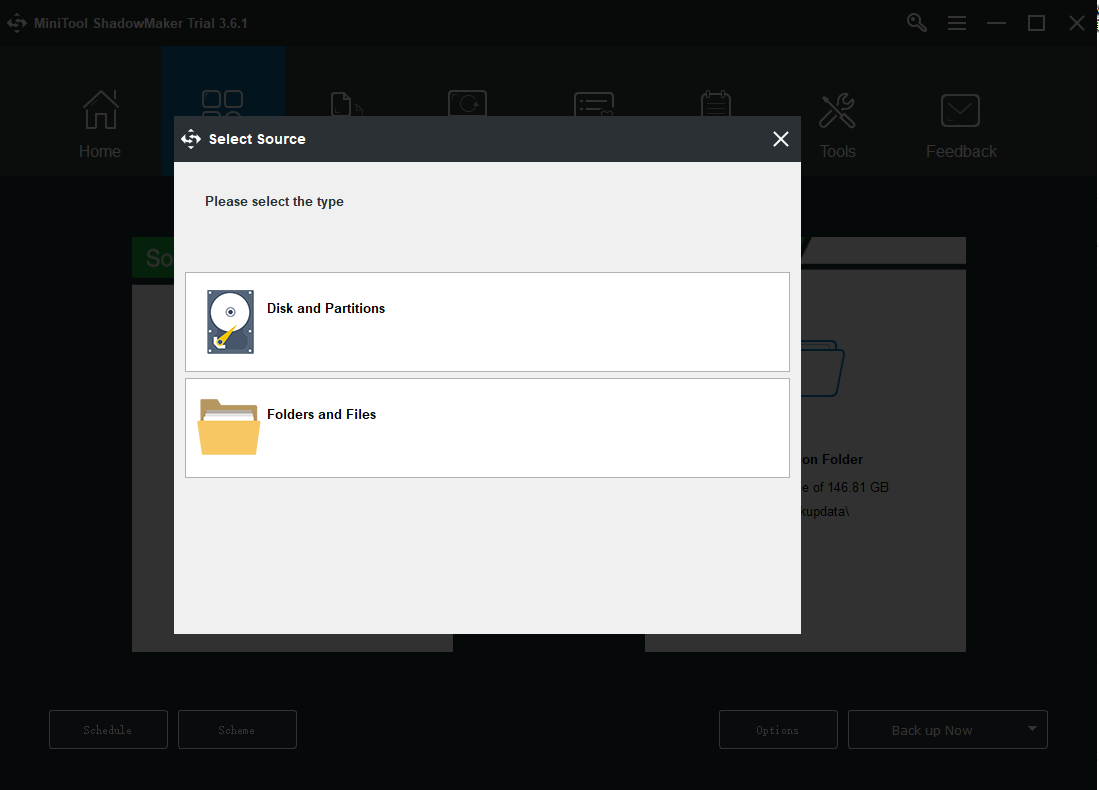
Step 3: To finish the backup, you need to click the Back up Now option to start the process immediately or the Back up Later option to delay the backup. The delayed backup task is on the Manage page.
Bottom Line:
All cyber attacks can make your data loss or privacy intrusion possible, which is hard to prevent. However, to avoid a more severe situation to happen, you can make a backup plan for all your important data. This article about DDoS vs DoS has introduced two common attacks. Hope your issue can be resolved.
If you have encountered any issues when using MiniTool ShadowMaker, you can leave a message in the following comment zone and we will reply as soon as possible. If you need any help when using MiniTool software, you may contact us via [email protected].
DDoS vs DoS FAQ
Because of its small scale and basic nature, ping-of-death attacks usually work best against smaller targets. For instance, the attacker can target a single computer or a wireless router. However, for this to be successful, the malicious hacker must first find out the IP address of the device.
In lost revenue and data, the cost of a DDoS attack on your tech business or your client's business can escalate quickly. The average small to medium-sized business spends $120,000 per attack.
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing them to slow down and eventually stop. Popular flood attacks include Buffer overflow attacks – the most common DoS attack.
This type of sporadic attack can vary in length, from short-term actions that last for a few minutes to longer strikes that exceed an hour. According to the DDoS Threat Landscape Report 2021 from Swedish telecom Telia Carrier, documented attacks average a 10-minute duration.


User Comments :