Recently, a new vulnerability called “PrintNightmare” is found on Windows systems. Microsoft warns users of all Windows versions to pay attention to this vulnerability since it is being frequently exploited by hackers to attack their systems. What’s the root cause for PrintNightmare? How should you respond to this vulnerability?
The New Vulnerability “PrintNightmare” – CVE-2021-34527
Recently, a new remote code execution vulnerability is found in Windows, causing a stir among Microsoft and multiple other entities. The vulnerability is dubbed “PrintNightmare” and Microsoft labels it as CVE-2021-34527 in its post on the company’s Security Update Guide. The PrintNightmare vulnerability gives attackers a chance to hack into Windows computers and execute code on these machines remotely.
A Serious Vulnerability Was Found In The Windows Task Scheduler.
What Causes PrintNightmare Vulnerability
Hackers are actively exploiting the PrintNightmare security flaw to access users’ devices to do many things: install apps, manipulate users’ data, and even create a new account with full privileges. The PrintNightmare vulnerability seems to be a result of the unpatched critical flaw in Windows Print Spooler. What is Print Spooler? It is a program that’s in charge of the printing on Windows computers.
Two vulnerabilities are involved in the Print Spooler flaw.
- Local privilege escalation: the hackers/attackers can get access to a compromised computer with only a low degree of privilege; then, authorize themselves with the admin or system level rights.
- Remote code execution: it makes local access and lateral movement into other systems (for example, a domain controller) easy jobs for the criminals.
MiniTool Power Data Recovery TrialClick to Download100%Clean & Safe
In fact, the vulnerability has been there for some time, but it’s not discovered until a few days ago when Sangfor security researchers published a proof-of-concept (POC) exploit accidentaly. They released a kit on Github talking about how to exploit the weakness, assuming that it had been addressed earlier in June, 2021 when Microsoft took measures to fix another Windows Spool issue. This is actually a mistake.
Though the test code was quickly deleted, it had already been forked on GitHub. Several days later, Microsoft noticed the flaw and issued an alert about it. Now, Microsoft warns Windows users of this potentially major zero-day security flaw in Windows Print Spooler service.
Till now, millions of Windows computers have been exposed to PrintNightmare related severe safety problems. How to protect your system from the problems? Microsoft is working on finding print spooler vulnerability fix and it recommends that users should disable the Windows Print Spooler service temporarily or update Windows to the latest version before a patch is finally released.
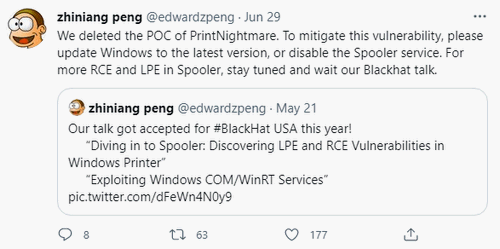
Disable Print Spooler Windows 10 Using PowerShell
Many users choose to disable the Spooler service on Windows 10 by using PowerShell commands so as to mitigate the PrintNightmare vulnerability.
- Press Windows + X or right click on the Start button.
- Select Windows PowerShell (Admin) from the WinX menu.
- Type Stop-Service -Name Spooler -Force into the PowerShell window.
- Press Enter to execute the command to stop Spooler service.
- Type Set-Service -Name Spooler -StartupType Disabled and press Enter to prevent Windows from re-enabling the service at startup.
[Fixed] WinX Menu Not Working In Windows 10.
How to Re-enable Print Spooler Using PowerShell
You’ll need to restart Print Spooler when the patch or fix is finally out. But how to restart printer spooler Windows 10 using PowerShell?
- Open Windows PowerShell as an administrator.
- Type Set-Service -Name Spooler -StartupType Automatic and press Enter.
- Type Start-Service -Name Spooler and press Enter.
Disable Print Spooler Windows 10 via Local Group Policy Editor
- Press Windows + S to open Windows search.
- Type gpedit.msc into the search box.
- Click gpedit.msc or press Enter to open the Local Group Policy Editor.
- Expand Computer Configuration and Administrative Templates. Then, select Printers in the left pane.
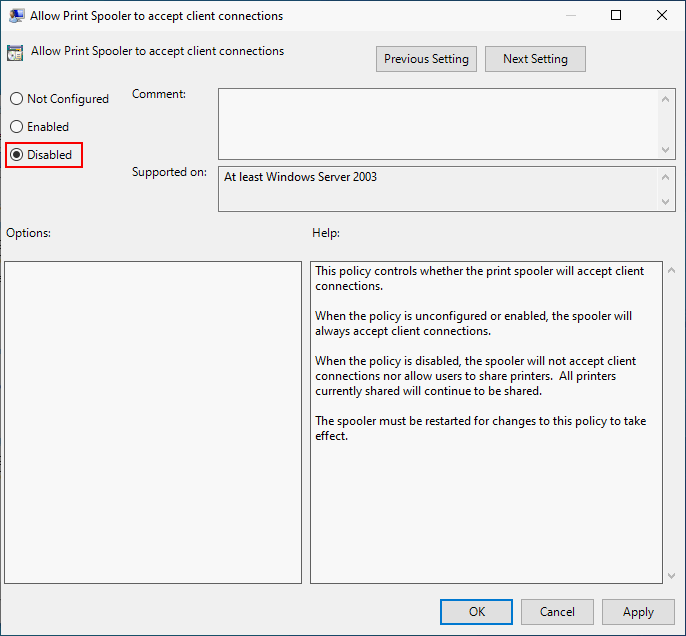
- Double click on Allow Print Spooler to accept client connections in the right pane.
- Check Disabled. Then, click Apply and OK to confirm the change.
How to Re-enable Print Spooler with Group Policy
Please follow this to finish Windows 10 restart Print Spooler:
- Open Local Group Policy Editor.
- Go to Computer Configuration -> Administrative Templates -> Printers.
- Double click on Allow Print Spooler to accept client connections.
- Check Not Configured. Then, click Apply and OK.

User Comments :