Trojan:Win32/Pomal!rfn
Trojan:Win32/Pomal!rfn is a detection commonly encountered when downloading programs. Once it infiltrates your system, it can serve as a gateway for additional threats, downloading and installing other malicious programs without the user’s knowledge, stealing sensitive information such as login credentials, cryptocurrency wallet keys, or other sensitive info.
The virus spreads through unsafe downloads, malicious email attachments, links in phishing emails, compromised websites, or fake updates or installers.
Sometimes, Microsoft Defender gives false positive reports, so be sure you download the file from a known or legitimate source.
Quick Fixes for Trojan:Win32/Pomal!rfn Removal
Solution 1. Uninstall Malicious Programs
Booting your PC into Safe Mode can help you safely uninstall problematic programs. To do so:
Step 1. Click on Start and choose Settings > Update & Security > select Recovery from the left pane.
Step 2. Click on Restart now under Advanced startup to enter Windows RE (recovery environment).
Step 3. Then select Troubleshoot > Advanced options > Startup Settings > Restart.
Step 4. Wait until the computer restarts, then press 4 or F4 to enter Safe Mode.
Step 5. Press Win + R to open the Run box and type appwiz.cpl and hit OK.
Step 6. Find the most recently installed programs or you don’t remember installing. Then uninstall them.
After the uninstallation, restart your computer to see if this move works.
Solution 2. Delete the Virus Files
You can also try delete those malicious files that cause you get the Trojan:Win32/Pomal!rfn.
Step 1. Press Win + E to launch File Explorer and go to the View tab to check Hidden items.
Step 2. Go to the location of the detected file. Then select it and delete it.
Solution 3. Reset Browsers Back to Default Settings
To remove settings changed by malware or malicious extensions, the best solution is resetting your browsers to their default settings. Here’s how to do it:
Step 1. In Google (example), click on the three-dot button in the top-right and choose Settings.
Step 2. In the left pane, select Reset settings > Restore settings to their original defaults >Reset settings.
Related article: How to Hard Refresh Chrome and Other Browsers? Here Is the Guide
Solution 4. Delete Windows Defender History
Performing a full system scan is essential when dealing with this type of malware. Here’s how to do it via Microsoft Defender:
Step 1. Click on the search bar and type Windows Security. Then press Enter to launch it.
Step 2. Choose Virus & threat protection from the sidebar and select Scan options under Current threats.
Step 3. Select Full scan and click on the Scan now button. This process will take a moment to complete.
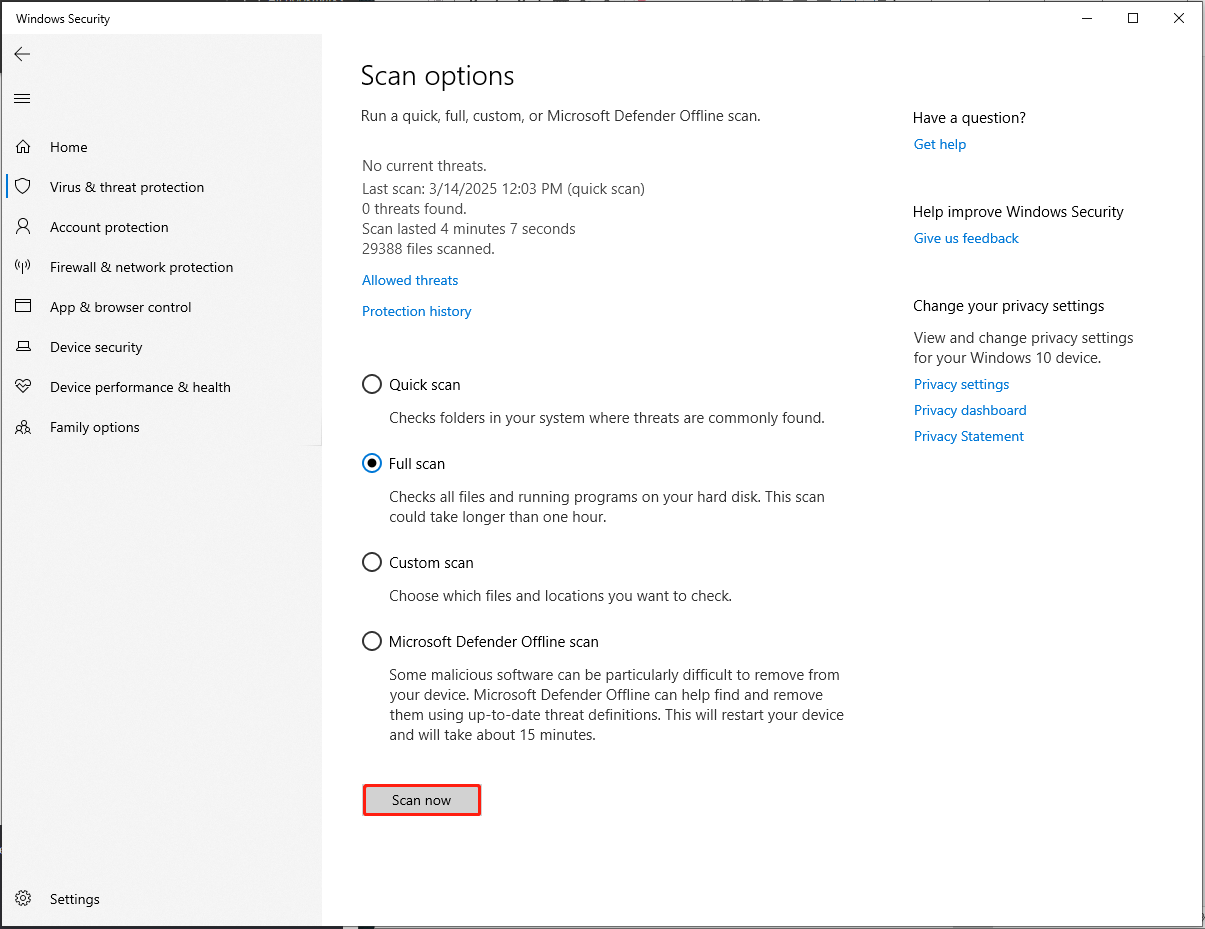
After the scan, restart your PC and check if the virus is removed or not.
And then, there’s a necessary step you have to do is to remove its scanning history. Follow the steps.
Step 1. Delete Windows Defender scan history which may include malicious files that were quarantined. Open File Explorer and follow the path: C:\ProgramData\Microsoft\Windows Defender.
Step 2. Locate the Quarantine folder and right-click on it to delete it.
Bonus Tip: Back up Your PC
Once your computer is invaded by one malware or virus, then your existing security may be broken by malicious cyberattacks easily. To avoid data loss or other disasters, it’s highly recommended you consider backing up your files or system. The backup image can help you restore your computer effectively.
Try using MiniTool ShadowMaker. This freeware is able to backup files, partitions, disks, and Windows system. Follow the simple tutorial to work with it.
Step 1. Download, install and launch MiniTool ShadowMaker.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2. Go to Backup > select SOURCE to pick up the items you need to back up > choose an external hard drive (recommended) as a storage path in DESTINATION.
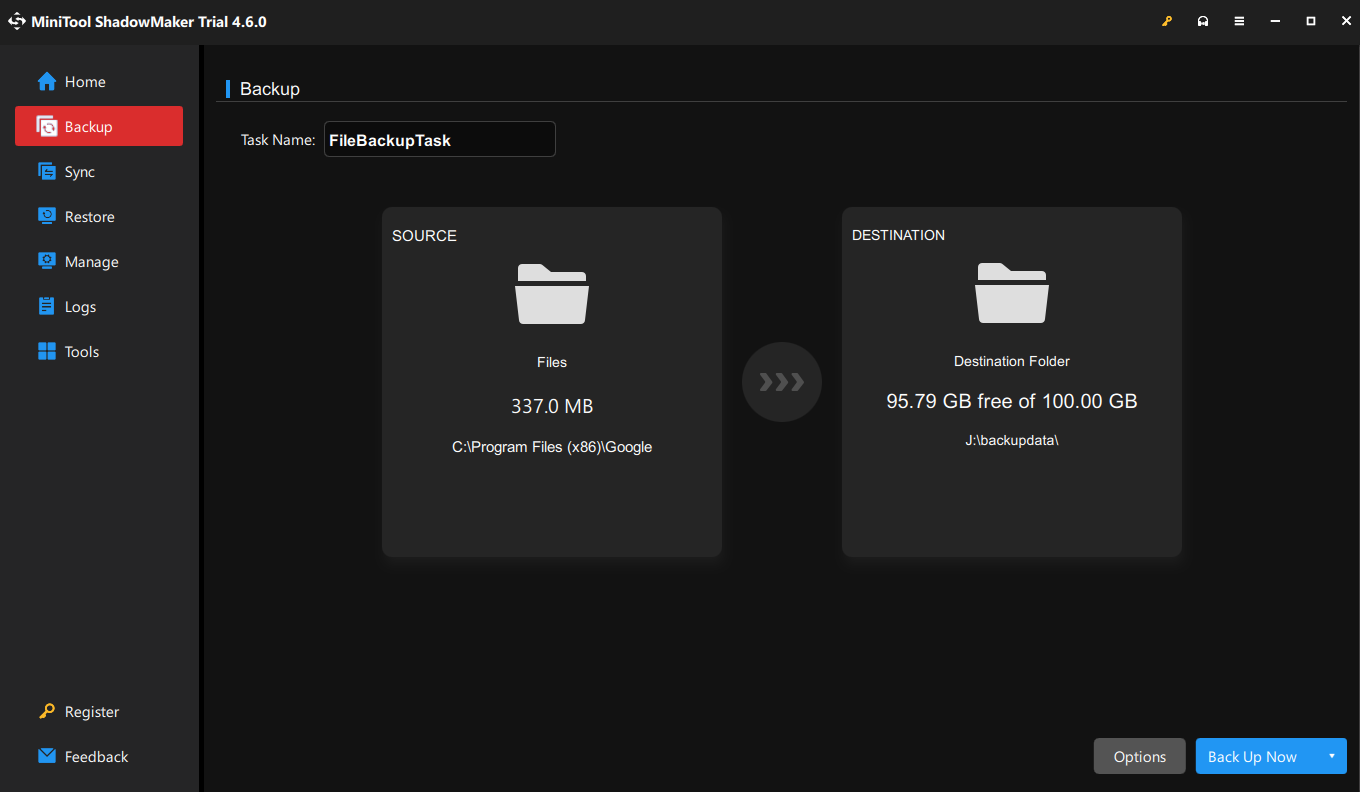
Step 3. Click on Back Up Now to start the process.
Wrapping Things Up
This guide contains several solutions for you to remove Trojan:Win32/Pomal!rfn. Besides, keep in mind that do not download software, or files from unknown sources or click suspicious email links.


User Comments :