Are you plagued with infostealer malware? How can you remove infostealers Windows 11/10? This guide on MiniTool will dive into the definition of infostealer malware and the ways to get out of it. Most importantly, you can learn to develop a backup habit to prevent unforeseen data loss.
What Is Infostealer Malware?
An infostealer is a type of malware designed to steal sensitive information on your device. Once the system is compromised, your information will be stolen, packaged, and traded on the dark web, including but not limited to login credentials, financial information, personal data, browser data, emails, and screenshots.
Infostealers often invade systems through phishing emails, malicious attachments, or infected websites. They operate so quiet that systems are hard to detect, posing a more serious risk of identity theft, financial loss, or unauthorized access to systems.
6 Measures to Take if Your Device Is Infected
After having a quick look at the definition of infostealer malware, you should know a single infection can lead to various potential problems. Once infected by infostealer malware, it’s urgent to immediately take action to limit the damage and prevent further damage.
Here we’ve listed several practical ways for you. Before proceeding, you should be made aware of the fact that infostealers are malware that is designed to evade detection and steal sensitive information from your device, including both work and personal data.
In this case, you should avoid using the device until the following have been completed. Now, let’s get started:
Move 1: Reset All of Your Passwords
First of all, you should change your passwords from a secure device, starting with your email, password manager, financial accounts, cloud services, and social media. If services support it, you should force a logout of all sessions so attackers can no longer access them.
Cybercriminals often continue to target users even after an initial infostealer infection. By using the stolen personal data, they can meticulously plan highly deceptive follow-up attacks, which are harder to detect. To reduce the risk of further damage, you should use a password manager, enable multi-factor authentication (MFA), and keep your device up to date as much as possible.
Then, you should inform your bank and close contacts about the infection. If the infected device was used for online banking operations, you should check and notice if there are any abnormal activities in your account, and contact your bank if you encounter any suspicious logins or payment behaviors.
Not only that, infostealers may have also stolen files stored on the device, such as passport photos, your browser’s history, and captured screenshots while the device was being used. Additional steps may need to be taken based on your stored files or device usage.
Move 2: Deeply Clear Your Device
The device should be cleaned before it can be used again to prevent the attacker from stealing credentials again.
#1
Use Windows Defender or existing antivirus software to perform a full system scan, detecting and removing the threats it finds on your device.
To do that, type Virus & threat protection in Windows Search > hit Enter > choose Scan options under Current threats > check Microsoft Defender Offline scan > click Scan now.
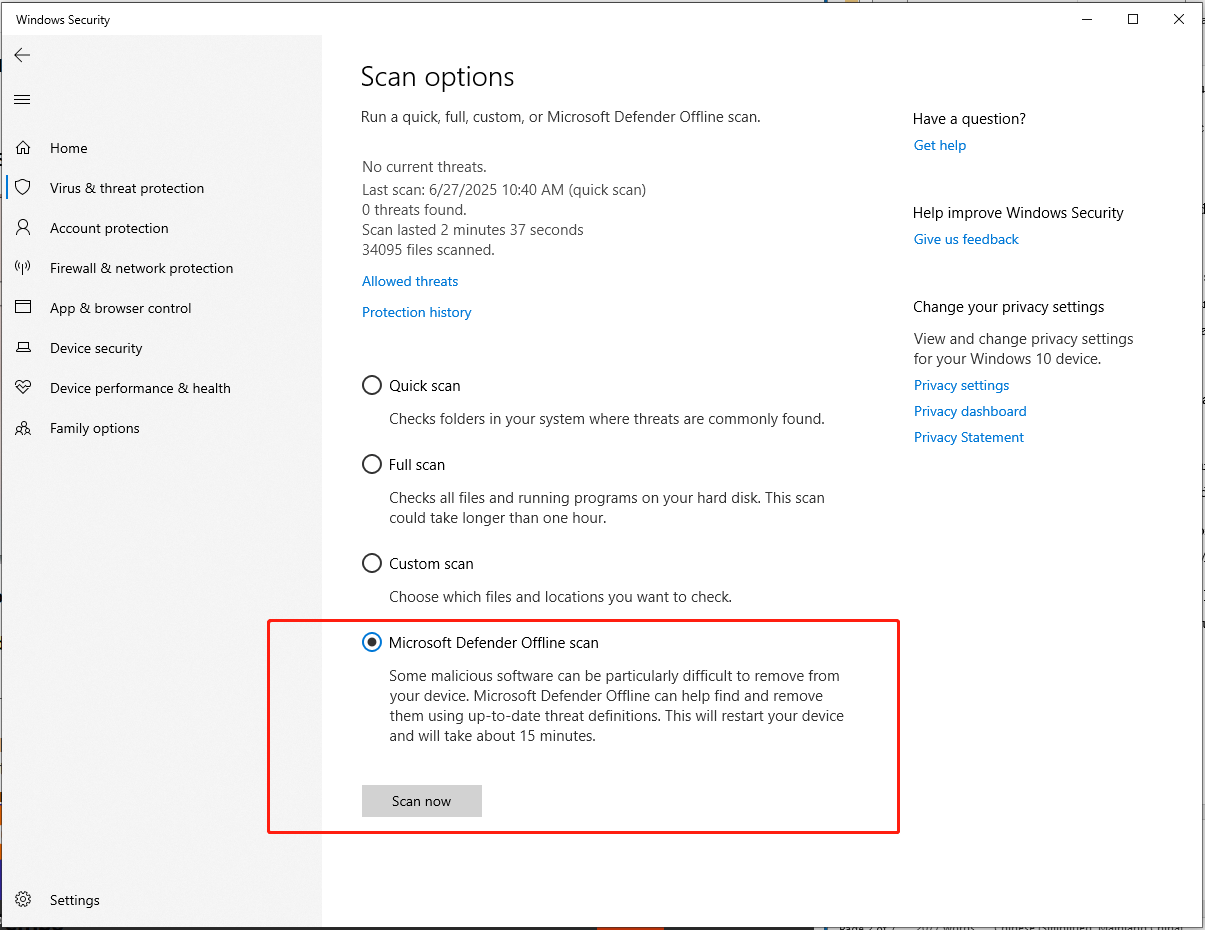
#2
Since infostealers may be disguised as software, you can try deleting suspicious apps to get rid of infostealers on Windows 11/10.
To do that, open Control Panel > look for Programs and Features > navigate to the software that you think is an infostealer > click on it > hit Uninstall.
After removing all problematic programs, you need to reboot your PC.
#3
Temp files are temporary files that the computer creates to open a program in a short time. Those folders are usually the directory where some malware such as infostealer malware, adware, and Trojans hide. What’s more, hackers also access your computer through Temps.
To remove an infostealer from PC by deleting Temps: Press Win + I to bring up Settings > select System > choose the Storage tab > scroll down to Temporary files > tap on Remove files after scanning.
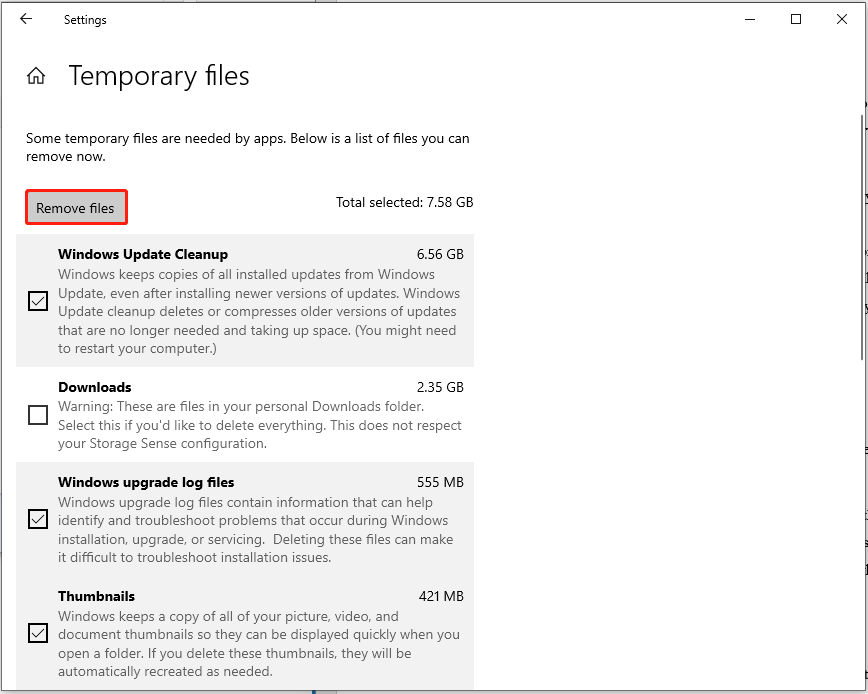
To delete Temp folder, press Win + E to open Files Explorer > browse to C:\WINDOWS\Temp > click Select All in the Home tab along the top of the window > hit Delete with all the files highlighted > restart your computer.
#4
You can install a trusted and robust antivirus solution, such as Malwarebytes and McAfee, to detect and remove infostealer malware.
#5
The last resort to remove infostealer malware is running a Windows factory reset. This operation enables you to remove all installed programs and system files, including the infostealer, and only reinstall the most basic and necessary apps and drivers from manufacturers.
To do so: Open Settings > click Update & Security > tap on Get started under Reset this PC > choose Keep my files or Remove everything.
You had better choose to delete all your files from Windows 11/10 in case the infostealer is still left in your system. This operation will wipe your system, so you must back up some important files and run them via a reliable antivirus tool before you copy them back to your system.
By the way, if some of you feel confused about the differences between Windows reset, clean install, and fresh start. Then you can move to the Windows reset vs clean install vs fresh start post to figure it out.
#6
Devices could have been infected for a period of time before it was detected, therefore, you should not restore your device from old backups unless you are sure they are clean.
3 Tricks to Prevent an Infostealer Infection
Tip 1: Look out for Strange Websites
Typically, malware masks itself as a pop-up and appears while browsing or running some apps. It entices you to open it, and even though you want to close the popping-up window, the system will download it at once as soon as you click the X button.
Therefore, pay attention to any unknown popping-up windows and don’t click them randomly.
To close it, you can go to Task Manager to find and end the app with malicious pop-ups. Then uninstall the app and delete the corresponding files, and your computer should become safe and sound.
Tip 2: Only Download Applications from the Official Channels
If you want to install any software, don’t download it from non-secure websites. In some cases, some unwanted and unnecessary apps may install automatically along with the target app if you download them from an unofficial site.
Also, viruses or other malicious malware adhering to the links of the strange websites make their way infect your PC, corrupting your system performance. Before opening a link, you can scan it with Virus Total to verify its security.
Tip 3: Develop the Habit of Backup
To resist the attack of malware like infostealers, it’s essential to develop a backup habit in case you need to rebuild your computer from ground. At the mention of backup, we strongly recommend a powerful backup software, MiniTool ShadowMaker. If you happen to get attacked by infostealer malware, don’t worry, you can rely on it to restore your data easily and quickly.
As a professional backup software, MiniTool ShadowMaker allows you to back up files/folders, partitions, and disks, and even the entire system. With a backup, you don’t need to worry about accidents like hard drive failures and system crashes due to malware attacks.
Now, let’s see how to back up the Windows OS with MiniTool ShadowMaker.
Step 1. Hit the button below to download and install the trial edition of MiniTool ShadowMaker.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2. Open it & click Keep Trial, and you will enjoy a 30-day backup service for free.
Step 3. In Backup, as you can see, your system has been selected in SOURCE. Head to DESTINATION to opt for a storage path for your backup. It’s recommended you choose an external hard drive or a USB flash drive.
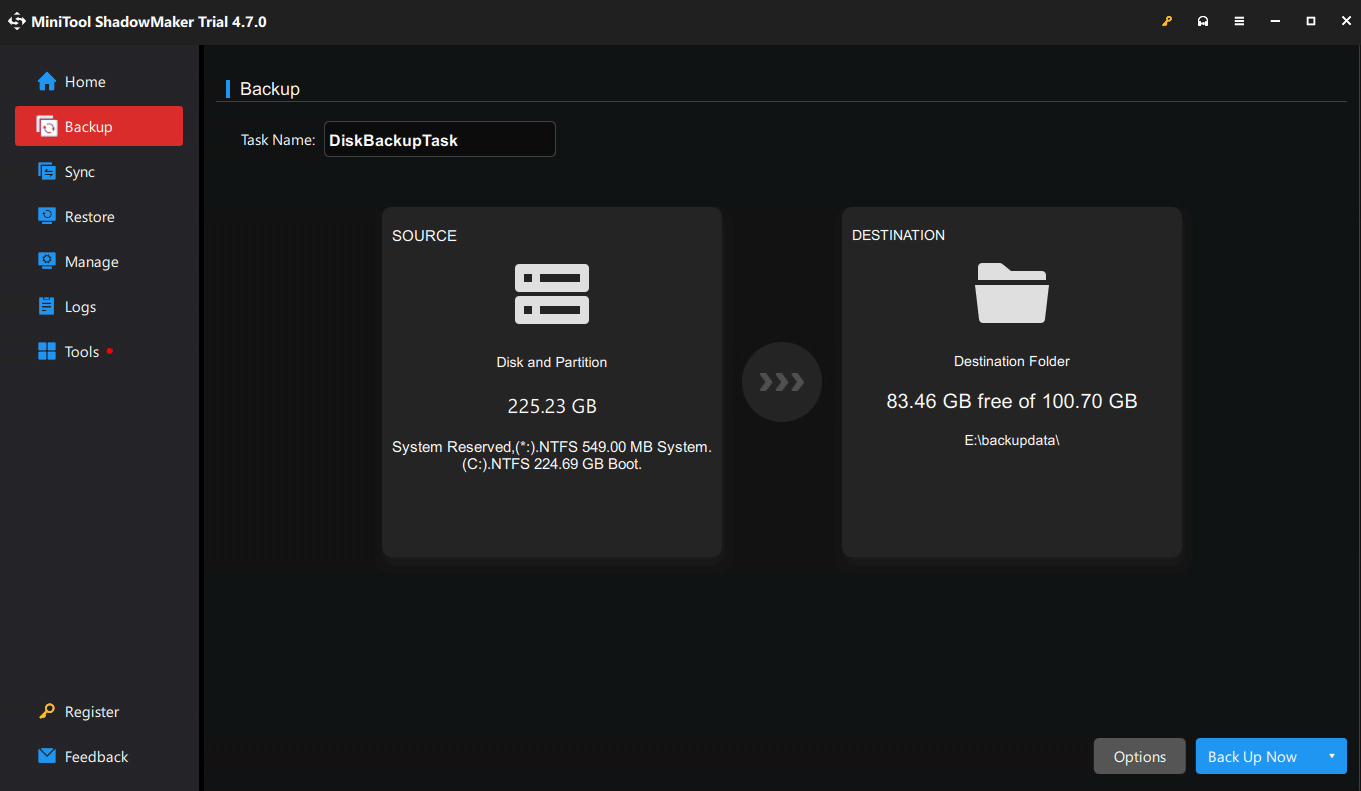
Step 4. Check all the settings and then click Back Up Now to start immediately.
Since backup is a long-term project, you might be tired of having to do the manual backup every time, but fret not, MiniTool ShadowMaker is so considerate that it enables you to make backups at a regular time.
You can set up an automatic backup after selecting the backup source and destination. Click Options in the lower left > toggle on Schedule Settings > schedule your backups on a regular basis, such as daily, weekly, monthly, or on a specific event > click on OK to save the settings.
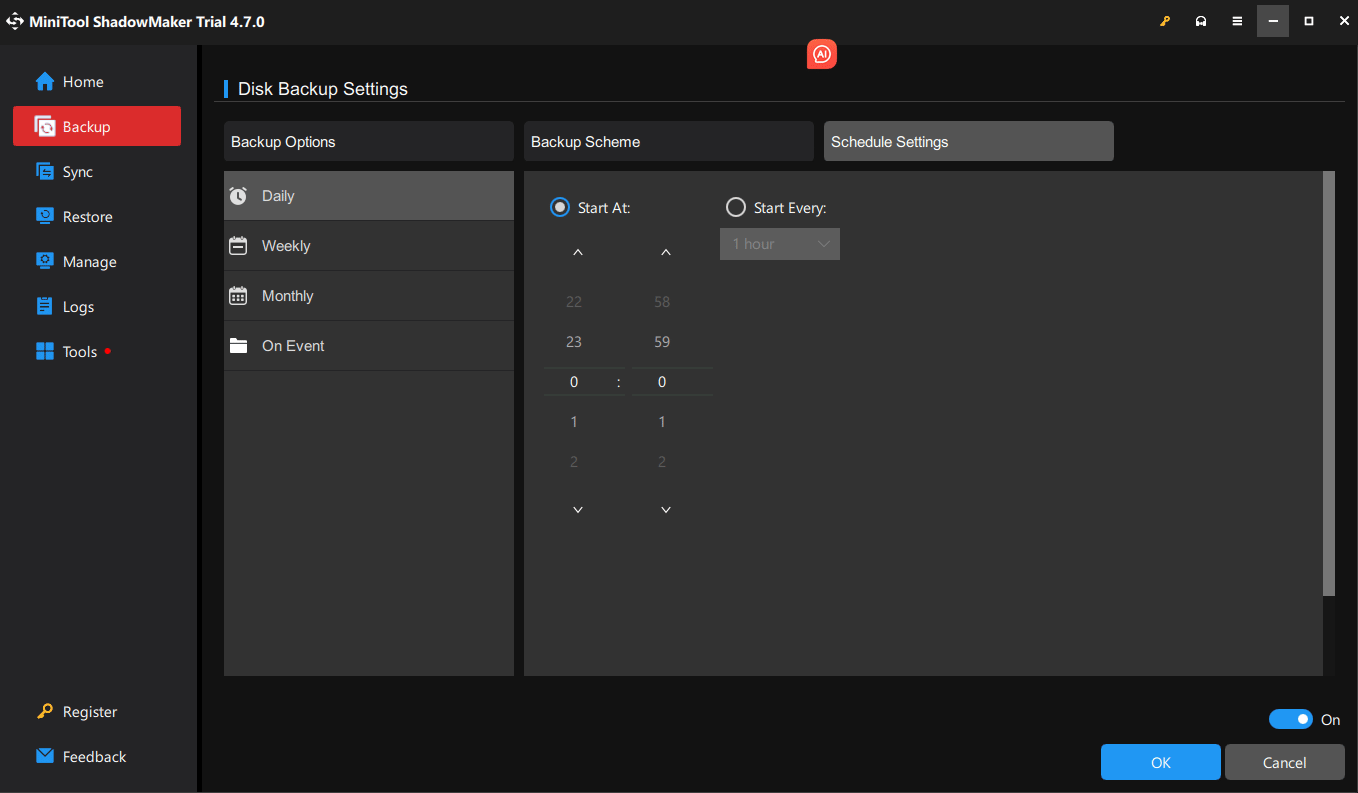
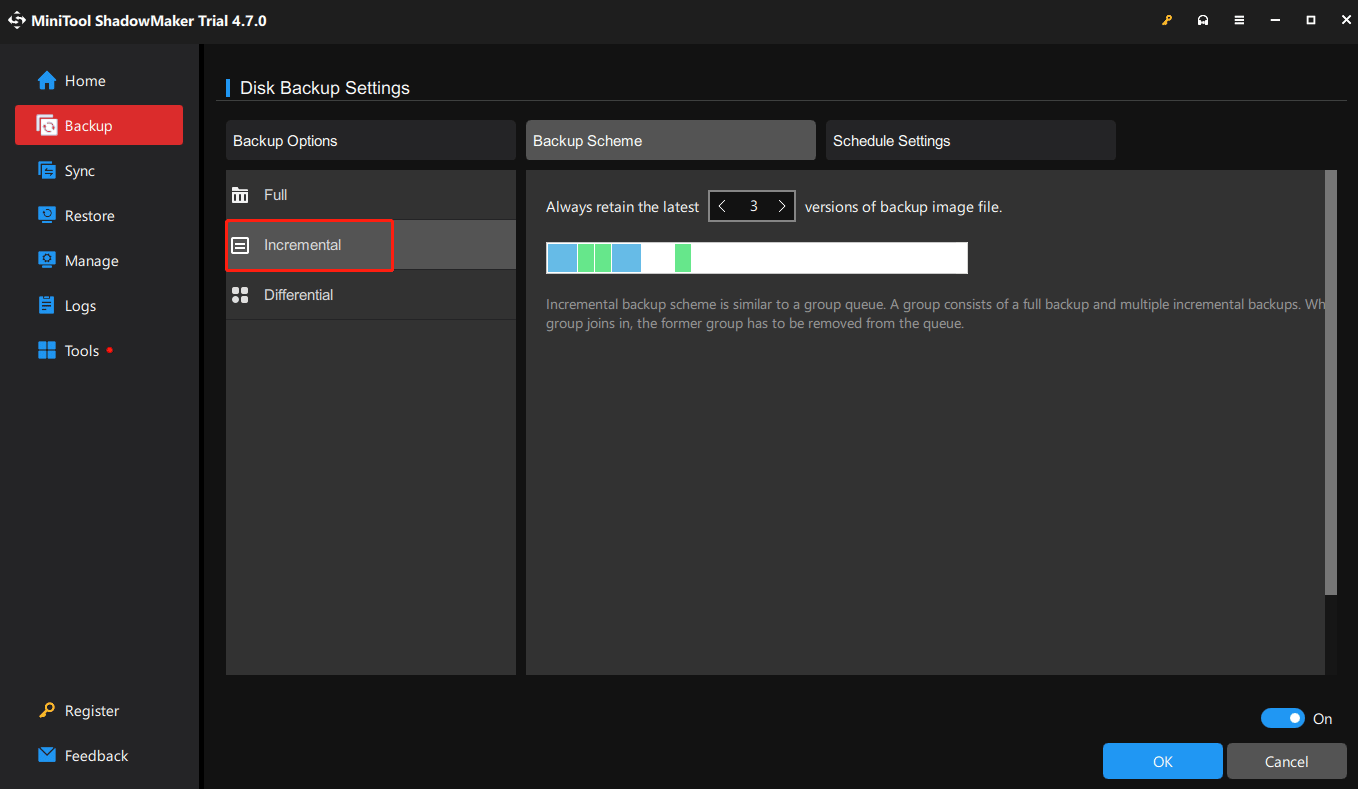
You may also worry these backup files will hog your drive space. For that, MiniTool ShadowMaker provides three backup types: full, differential, and incremental backup. The incremental backup scheme helps you save your storage space to the greatest extent.
To configure it, go to Options > turn on Backup Scheme (disabled by default) > choose Incremental > click on OK to save the settings.
Bottom Line
To sum up, we introduce you that what infostealer malware is, how to perform infostealer malware removal, how to prevent this malware, and most importantly, how to set up a regular backup task with MiniTool ShadowMaker to prevent data loss caused by infostealer malware. Sincerely hope that all the tricks and tips do the charm for you.
If you have any confusion about MiniTool ShadowMaker, comment below or send an email to [email protected]. We’ll reply to you as soon as possible.
Infostealer Malware FAQ
2. Do not open up any unknown pop-ups, links, or attachments.
3. Enable multi-factor authentication (MFA) for your accounts.
4. Never download applications from non-secure channels.
5. Always keep backups in multiple locations and adopt the 3-2-1-0 backup rule.
2. You’re inundated with popups.
3. Your browser keeps getting redirected.
4. Strange messages sent from your social media accounts.
5. Internet traffic suspiciously increases.
6. A red warning window shows up on web pages.
7. Renamed files.
8. Inexplicable loss of disk space.
9. More…
2. Reset browsers: Clear cache, cookies, and reset settings to defaults to remove hijackers.
3. Review installed programs: Uninstall any suspicious or unrecognized programs via Task Manager.
4. Factory reset system: Give your computer a fresh start and restore from a clean backup made before infection, if you have.
5. Change passwords: Modify all your critical accounts on a trusted network after the system is clean.


![[Various Definitions] What Is Bloatware on a Computer or Phone?](https://images.minitool.com/minitool.com/images/uploads/2020/03/remove-windows-10-bloatware-thumbnail.jpg)
User Comments :