Microsoft has noticed a new zero-day flaw which can attack Windows 10 and some versions of Windows Server systems. Microsoft warns users of this security vulnerability and offers some feasible workarounds to mitigate the attack. MiniTool Solution will introduce the new zero-day vulnerability found a few days ago and list the feasible mitigation methods.
Hackers Can Attack Your Windows via CVE-2021-40444
Recently, a new zero-day flaw was found by people. Hackers can take vantage of it to attack Windows 10 and some versions of Windows Server computers. Till now, there’s still no official security update to patch your system. However, Microsoft has warned users of this security vulnerability and provided some useful workarounds to mitigate the attack.
The new zero-day vulnerability is known as CVE-2021-40444. Hackers and attackers are exploiting it to execute code on the target computer remotely; even worse, they could seize complete control over the PC.
New Windows Print Spooler “PrintNightmare” Vulnerability Is Found.
MiniTool Power Data Recovery TrialClick to Download100%Clean & Safe
Attackers Are Exploiting Internet Explorer & Microsoft Office Documents
According to search, the security flaw CVE-2021-40444 can attack the MSHTML part in Internet Explorer browser rendering engine running on Windows 10 and several Windows Server computers. However, if you think you’re safe since you never used Internet Explorer, you’re totally wrong. Why? That is because Microsoft Office is also affected by the remote code execution vulnerability.
The same vulnerable component – the rendering engine – is also used by Microsoft Office applications for rendering web-based content. Therefore, if you unfortunately open the trapped websites or specially-crafted Microsoft Office documents, you’ll get attacked.
- The MSHTML will be loaded when users open Office documents (.docx filetypes).
- Then, a specially constructed malicious web page will be displayed.
- The ActiveX control will be employed to take the system to download the malware payload.

Attention:
The MSHTML remote code execution vulnerability will leave less impact on users without administrator rights than those with greater privileges.
You Can Get Admin Privileges On Windows 10 With A Razer Mouse.
Microsoft Warned Windows Users of CVE-2021-40444 & Provides Mitigations
On the morning of Sunday, 5 September, 2021, a researcher at EXPMON reported this Windows security vulnerability to Microsoft. Then, Microsoft released the page “Microsoft MSHTML Remote Code Execution Vulnerability” on its website to explain CVE-2021-40444 and offer exploitability, mitigations, workarounds, and more. Don’t worry; Microsoft is still working on this and will release a security update to patch the hole very soon as part of the Patch Tuesday cycle, or even as an out-of-band update beforehand.

All Windows 10 and Windows Server users should take speedy mitigation action until an official patch is out.
How to Mitigate the New Security Attack
Microsoft mainly gives 2 suggestions on mitigating CVE-2021-40444 currently.
#1. Update Antimalware Products
Users should enable and keep Microsoft Defender Antivirus & Microsoft Defender for Endpoint up to date on their computers. These two products both provide detection and protections for the known vulnerability.
- If you have enabled Windows automatic updates already, you don’t need to take additional action.
- For enterprise users who choose to manage updates manually, they should select the detection build 1.349.22.0 or newer. Then, deploy it ASAP.
#2. Disable Internet Explorer ActiveX Controls
Microsoft said disabling the installation of all ActiveX controls in Internet Explorer works well in mitigating the known attack. After that, the ActiveX controls installed previously on your PC will not expose this vulnerability, but they will still run.
How to disable ActiveX controls via Group Policy:
- Open Group Policy Editor on Windows 10.
- Go to Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page in the left pane.
- Double click on Internet Zone in the right pane.
- Double click Download signed ActiveX controls.
- Check Disabled and click OK.
- Repeat step 3 ~ 5 to all the zones in the list to fully protect your system.
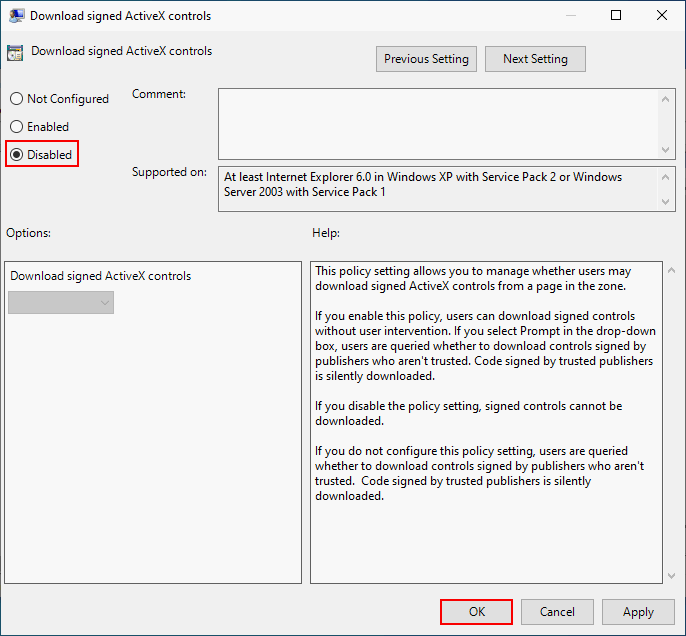
Also, you can disable ActiveX controls on an individual system via regkey or disable preview in Windows Explorer to further safeguard.
User Comments :