It’s good that you take some measures to protect your computer and data. However, if you make cybersecurity mistakes, the result will turn out to be just opposite of your wish. Now, follow this post on MiniTool to check if you have such errors and take the initiative to correct them.
What Is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. The cyberattacks are usually aimed at accessing, changing and destroying sensitive information, extorting money from users via ransomware.
Today, however, implementing effective cybersecurity measures is challenging because there are more advanced devices, and attackers are becoming more innovative.
Besides, people will also make some cybersecurity mistakes, which further aggravates the dangers of their digital lives. Now, let’s take a close look at what common pitfalls are.
Common Cybersecurity Mistakes & How to Avoid Cybersecurity Pitfalls
1. Use Weak, Reused, or Same Passwords
One of the most common cybersecurity mistakes made by enterprises and individuals often arises from passwords that are weak, easy to guess, reused, or in sequential order. The password is the first line of defense for all online accounts. Even so, there are still many users who either cannot come up with strong passwords or reuse the same password on multiple platforms.
All these increase the risk of passwords being cracked by hackers and may lead to data loss. If hackers use algorithms to try millions of combinations, weak or reused passwords can be easily cracked.
For instance, if a hacker makes a way to invade your email account and you use the same password for online bank, you actually give the hacker an advantage. This makes it possible for all your accounts to be threatened just by hacking into one account.
How to Avoid:
- Never reuse passwords.
- Set a unique and strong password for each account, combining uppercase and lowercase letters, numbers, and special characters.
- Do not use easily guessable information such as birthdays, names, etc.
- Enable multi-factor authentication (MFA) to enhance security.
- Try new password combinations every six months or so.
Although remembering so many passwords may be difficult, reducing the risks attackers getting access to your account is worth it.
Furthermore, it’s highly suggested you prepare a recovery plan before the problem occurs, since you might be locked out of your account for a long time. You can add a recovery email address or phone number so that you can be reached if your account is locked. By doing so, you can build a strong digital defense.
2. Outdated Software
Another common cybersecurity blunder is to postpone software updates. Postponing updates makes your system vulnerable to hackers’ inbreak and attacks, exposing your devices, data, and privacy to risks. Hackers always look for system loopholes to invade your devices and launch attacks.
Moreover, if you delay the update, some of them will execute automatically, often at inconvenient times. This may disrupt your workflow, and sometimes even cause programs to crash.
How to Avoid:
- Once the new version becomes available, update the software immediately.
- Set up automatic update functions for the operating system and applications.
- Regularly update the software on your devices.
It is of importance to update software timely as that is indispensable for maintaining a healthy and safe digital life. Updates usually contain protection measures and crucial security patches for fixing bugs and issues. Not all software systems automatically search for new versions, so sometimes, you need to look for updates manually.
In any environment, investing in update can ensure that the system remains secure and reduces the risks brought by security vulnerabilities.
3. Lack of Multi-Factor Authentication
Multi-Factor Authentication (MFA), is a security feature that adds an extra layer of security for sensitive data during login. This requires multiple identity verification to verify the user’s identity, usually including a password, fingerprints or facial recognition. It helps prevent unauthorized access to your account unless you allow it.
Some individuals and even enterprises may overlook this simple and effective feature because they don’t want to go through multiple verification steps. However, this multi-level tool reduces the possibility of being hacked, even if the password is compromised.
How to Avoid:
Most systems or software require users to enter their account settings, select MFA or two-factor authentication, and choose a method, such as email, SMS or an authentication app. When enabling it, it will send prompts on your mobile device to allow login attempts.
Although using MFA for login requires a bit more time and effort, it significantly enhances security and avoids potential data leaks. It’s like adding a second lock to your digital life.
4. Lack of Security Awareness Training
Human error remains the main cause of cybersecurity issues. This way, one of computer security mistakes is insufficient employee training is no longer strange. Enterprises or organizations often purchase the latest and most powerful security technologies and systems on the market, but fail to realize that employees are one of the most serious cybersecurity threats.
If your employees don’t know when to keep an eye on suspicious activities and how to respond, then you have left a huge risk gap for yourself. Without proper training, they may unintentionally expose the company to hackers.
How to Avoid:
- Provide employees with training on how to avoid being attacked by hackers.
- Regularly conduct training courses on identifying attack methods such as phishing, email intrusion, and malware, and how to protect sensitive information.
- Combine with the actual situation of the enterprise to achieve the best training effect.
5. Click Suspicious Links and Email Attachments
One of cybersecurity mistakes is falling for phishing scams. Cybercriminals often disguise malicious links as legitimate ones, making it difficult to distinguish the genuine from the fake. In today’s digital environment, malicious links can appear in seemingly legitimate emails or harmless posts on social media. If you are not cautious enough, all of these can become channels for malware and hackers.
Cybercriminals exploit human fear, urgency, or curiosity to manipulate potential victims. For instance, an email claiming to be from your bank might ask you to immediately verify your account details to avoid having your account suspended. Clicking on the link might lead you to a fraudulent webpage designed to steal your information.
Therefore, phishing attacks remain one of the most effective methods for cybercriminals to steal sensitive info. How to avoid phishing emails?
How to Avoid:
- Stay vigilant. Before opening a link from an email or message from an unknown source, hover over it to view the URL and verify the identity of the sender, even if it seems legitimate.
- Reduce phishing emails in your inbox by using spam filters.
- Try to understand common phishing tactics and keep abreast of new fraud methods.
- Ensure the security of your devices by downloading the latest antivirus software.
6. Use Unsecured Public Wi-Fi
Wi-Fi is both a convenience and a potential hazard. Hackers can monitor users who are using unencrypted public Wi-Fi networks, thereby obtaining users’ private information.
When a person connects to a public Wi-Fi network, all his passwords, emails, credit card details, and every online activity he conducts on that network will be obtained by others on the network.
How to Avoid:
- Do not access your personal information on public Wi-Fi networks. When you have to connect to a public Wi-Fi, make sure to do so through a VPN that encrypts data transmission to protect your privacy.
- Use your mobile phone’s data network as it is often safer.
7. Underestimate the Threats
Social media has become a treasure trove for cybercriminals to obtain a large amount of personal information. From birthdays and addresses, sharing sensitive info without proper encryption exposes you to information leakage and privacy infringement.
All the trivial details shared online can be fully exploited. Usually, hackers and scammers will use centralized sources to answer security questions, send phishing emails and commit fraud. For instance, if someone posts information about an upcoming trip, they will discover that a specific family is temporarily unoccupied.
How to Avoid:
- Do not share sensitive information such as complete birth dates, home addresses or phone numbers.
- Use privacy settings to restrict who can view your posts and personal details.
- When receiving friend requests, make sure you know the person and trust them.
- Encrypt files and sensitive emails for additional protection.
8. Rely on Antivirus Alone
Relying on antivirus only can be cybersecurity mistakes. Antivirus software has always been the gold standard in cybersecurity. It helps to scan files to look for known viruses, and some even have service to deal with malicious software.
However, the attacks of cybercriminals keep evolving and improving. Although antivirus still has some effect, cybersecurity strategies should not rely solely on it.
How to Avoid:
- Make sure your antivirus software is always up-to-date.
- Enable popup blocker to prevent unsafe links from appearing on your screen.
- Never disable Windows User Account Control (UAC) even though it may be annoying. If you disable notifications, you provide hackers a blank check because they will be able to make changes to your computer without your permission.
9. Overlook Data Backup
Cyberattacks may cause damage or loss of your data. Moreover, once some attacks wreak havoc on your digital life, prompt action is crucial for minimizing the consequences. However, if you haven’t made data backup for your devices and don’t know how to recover from these disasters, the damage could be serious.
How to Avoid:
- Create backups for your computer and crucial data.
- Make a protection plan you will take and ensure that it is accessible in an emergency.
Protect Your Data with MiniTool ShadowMaker
In response to data protection and disaster recovery plan, we strongly recommend you create a system image for your PC. By doing so, no matter your computer breaks down for any reason, you can always bring it back to life with the system image you created.
Speaking of system backup, a piece of PC backup software called MiniTool ShadowMaker really deserves a try. Simple to follow and use, this free program is perfect for novice users. It’s known for one-click system backup solution that creates a complete snapshot of your current operating system.
Besides system backup, file sync, partition backup, data backup, disk backup, and disk cloning are also supportive.
Here’s a detailed tutorial on how to regularly back up your system using MiniTool ShadowMaker.
Step 1. Download, install, and launch this 30-day free trial to enter its main interface.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2. Head over to the Backup page. As you can see, the system-required partitions are selected by default in SOURCE, so you can only go to DESTINATION to choose a storage path.
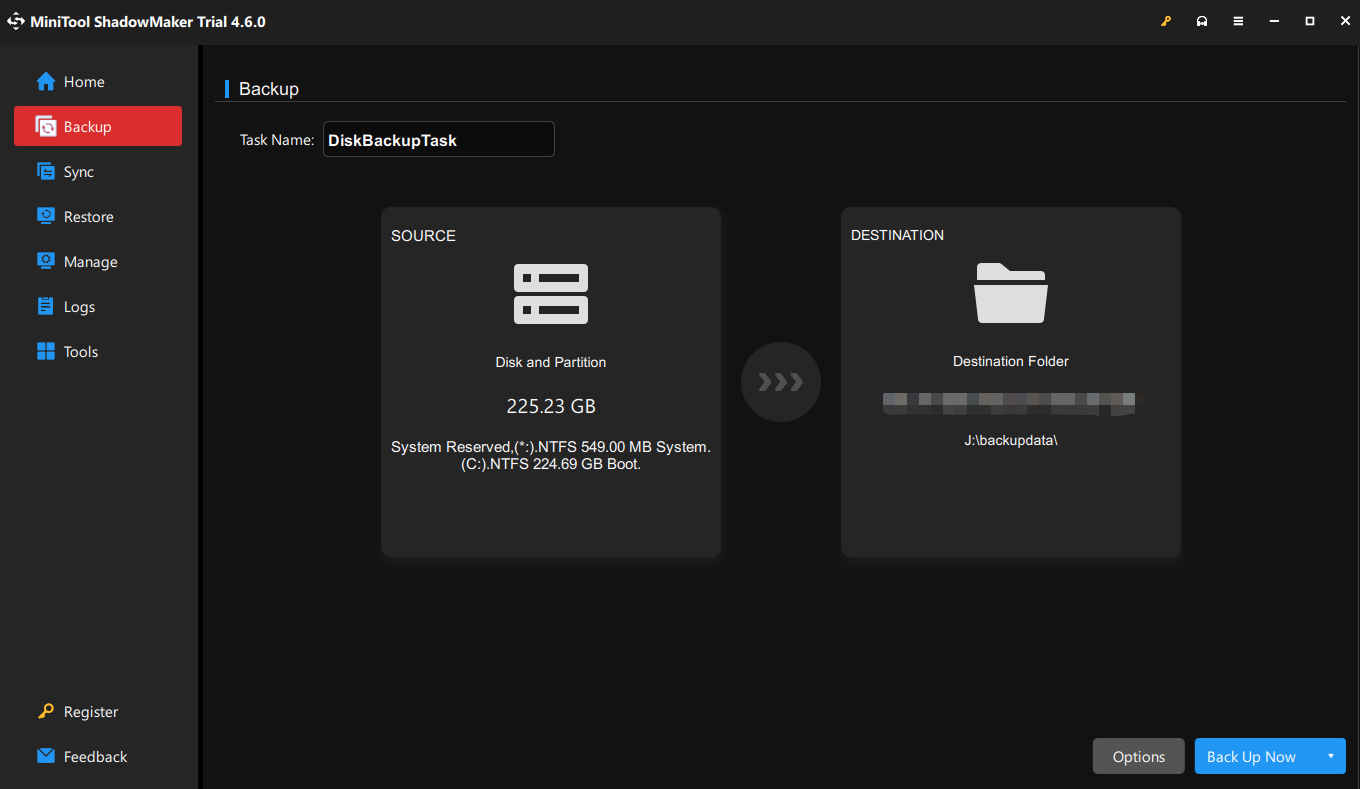
To back up files, go to SOURCE > Folders and Files > choose the content you need.
Step 3. Since backup is a long-term thing, it’s highly recommended you schedule the backup task. Click on Options at the lower-right corner.
① Set advanced parameters in Backup Options as per your needs.
② Toggle on Backup Scheme > choose an appropriate backup mode to save your space and time.
③ Toggle on Schedule Settings > pick up a time point to back up your data daily, weekly, monthly, or on events.
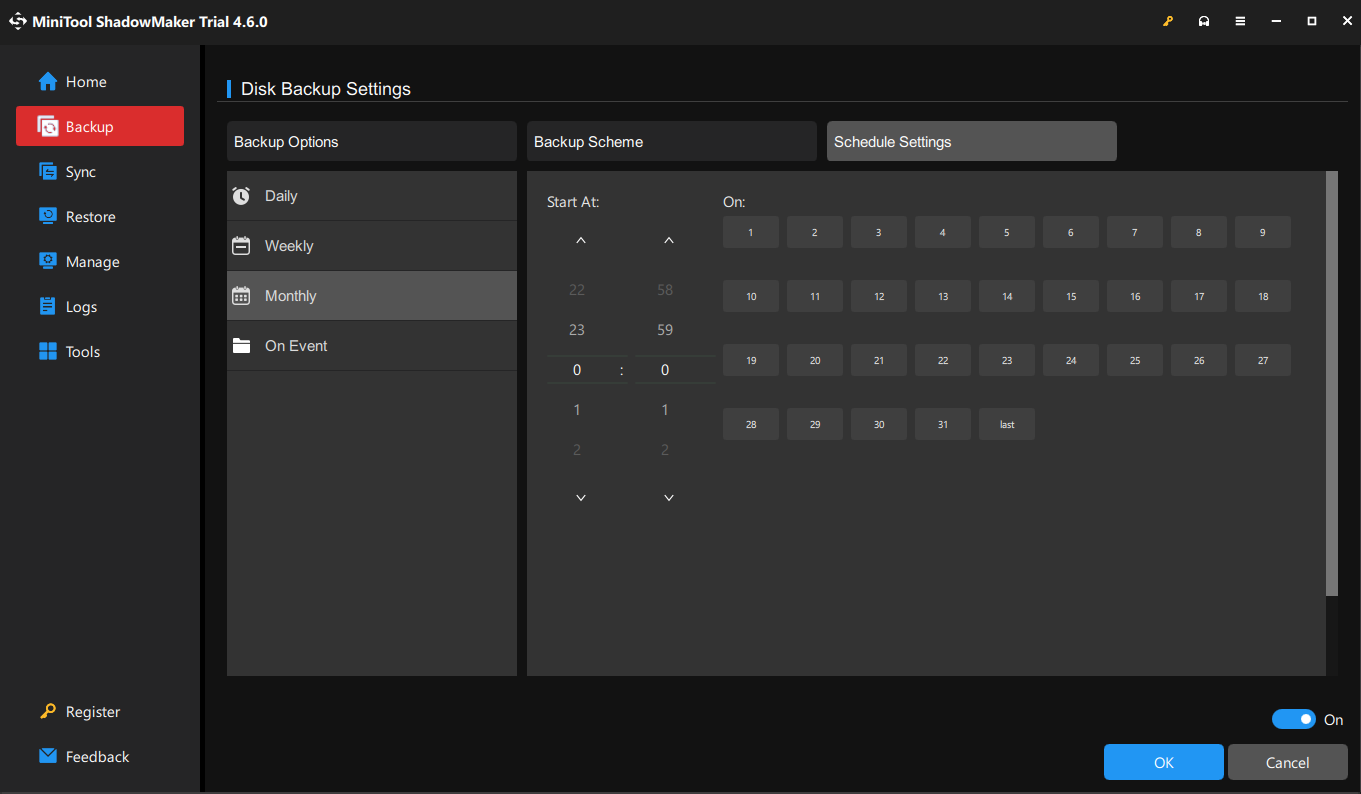
Step 4. Click on Back Up Now to initiate the process immediately.
Final Thoughts
After reading this guide, you might understand it is essential to be vigilant and proactive in a world which cyber threats are evolving. You must understand what common cybersecurity mistakes are and comply with basic data security principles like using strong passwords, being wary of attachments in email, backing up data, and more.
If there are any difficulties or worries while using MiniTool ShadowMaker, please don’t hesitate to contact our support team via [email protected]. We’re glad to help you.




User Comments :