What is the difference between the virus and worm? If you are looking for the answer to this question, you come to the right place. MiniTool Solution will provide information about the virus vs worm for you and you can know how to protect your computer from being infected by them.
Both virus and worm can destroy your computer, but they are different. If you want to learn more information about the similarities and differences between the virus and worm, please continue to read the following part.
Virus VS Worm
Here is a quick guide on virus vs worm.
| Virus | Worm | |
| Definition | A malicious executable code, which is attached to another executable file. The code may be harmless or can modify or delete data | A self-replicating malware that can be spread to different computers through the network |
| Purpose | Modify information | Consume system resources |
| Executing way | Execute via an executable file | Execute through weaknesses in the system |
| Spreading mode | Need host to spread | Does not require a host to copy from one computer to another |
| Removing method | Antivirus software and firewall | Antivirus software and firewall |
| Remote Control | Yes | No |
| Spreading speed | Slower | Faster |
| Examples | Resident and non-resident viruses | Morris Worm, Storm Worm, and SQL Slammer, etc. |
Now, let’s get more detailed information about worm vs virus. The main similarity is that both viruses and worms can replicate themselves and spread quickly. The differences between them are outlined below.
Definition
The first aspect of virus vs worm is the definition.
Virus
Computer viruses are programs composed of malicious code that can spread between devices. When your computer is infected by the virus, it can also change the way the computer runs, damage files, or prevent the file from running altogether.
Viruses usually attach themselves to programs, files, or the boot sector of the hard drive. When the infected application or file is running on the computer, the virus will be activated and executed in the system. It continues to copy and spread by attaching a copy of itself to other files and applications in the system.
Worm
A worm is a self-replicating malware (and a virus) that quickly moves from one computer to another by exploiting vulnerabilities to enter the network. Worms can not only spread locally but also damage systems all over the world.
Unlike typical viruses, worms do not attach to files or programs. Instead, they will tandem and enter the computer through loopholes in the network, replicate and spread themselves, and then delete the data. But by then, they have consumed all the bandwidth of the network, thereby disrupting and arresting large networks and web servers.
Spreading Ways
Viruses and worms use a variety of methods to spread throughout the network, including the following:
Email: Email is the most popular delivery method for malware, and can include infected attachments and malicious links containing viruses or worms.
Internet: The virus or Worm may spread by linking to the infected website. They usually hide in the HTML of the website, so the infection is triggered when the page loads.
Download and FTP server: Initially it may start with a downloaded file or a single FTP file, but if it is not detected, it can be propagated to the server.
Instant Messaging (IM): Transmitted via mobile and desktop messaging applications, usually as an external link, including native SMS applications, WhatsApp, Facebook Messenger, etc.
P2P/file sharing: Spread through the P2P file-sharing network and any other shared drives or files (such as USB memory sticks or network servers).
Network: They may also hide in network packets.
Now, you have known the details about computer worm vs virus: spreading ways.
Examples
The next aspect of computer virus vs worm is the example.
Virus:
You received an email with a header and attachment. The attachment to the email is a file with a name – it can be a doc or exe file.
If it is a doc file, once you download it, you will be prompted to enable the macro. This action will trigger a virus. If the file is an exe, downloading and running it will trigger a virus. The virus then controls the computer’s resources to replicate and spread itself, thereby damaging your equipment and files or stealing your data.
Worm:
You are notified that Windows has important security updates. This update is designed to fix a security vulnerability, but because you have not applied this update, the vulnerability (vulnerability) remains in the system.
Hackers will find this vulnerability and use it. Then, when you are busy with work or playing games, the worm will penetrate into your computer and start copying itself, thereby destroying your data and causing various other damages.
Blended threats:
The most dangerous cyber threats are those that combine different types of malware. In addition to the examples of viruses and worms, there are also examples of blended threats. An example of a blended threat is the use of Trojan horses (disguised as useful malicious code) to infiltrate viruses.
WannaCry is another example of the extreme damage that causes hybrid threats worldwide. It combines all aspects of worm and ransomware. Once WannaCry infects your computer, it encrypts your files and demands a ransom to release them. Then, WannaCry scans the network for other devices with the same security vulnerabilities. Once WannaCry finds devices, it will install itself on the new device immediately and repeat the process.
Which One Is More Dangerous
After getting the information about virus vs worm in different aspects, you may wonder which one is more dangerous.
Although there may be a certain degree of danger between viruses and worms, worms are generally considered more dangerous. Worms are sneaky because they may infect you even without your knowledge. Nowadays, it is difficult to find a new virus (or file infector) virus, and worms are more common.
Both worms and viruses have great potential to cause security and privacy issues. A minor malware infection can damage files, programs, or devices. Yet more damaging infections will steal your sensitive personal data, which can lead to identity fraud and money theft.
All in all, viruses and worms can cause large-scale data leakage, data loss or theft, expensive repair costs, reputation damage, and even cyber warfare.
How to Determine If You Have Been Infected
This part will introduce how to determine if your computers have been infected by the virus or worm. If you find the following signs, your devices may be infected.
- Unexplainable slow performance.
- Changed settings or new apps that you didn’t configure yourself.
- Computer crashes or freezes.
- File loss or damage.
- Multi-action processor.
- Sudden loss of storage space.
- Lots of pop-up windows.
Also see:
- How to Know If Your Computer Has a Virus: Signs of Infection
- How to Remove Virus from Laptop Without Antivirus Software
How to Avoid Virus and Worm
Here are some simple ways to protect your computer from being infected by the virus and worm.
1. Avoid Opening Suspicious Emails and Links
Do not open emails from unknown sources, even if the emails are from trusted contacts. Their device may be infected with malware that is sending spam to their contacts. Pay attention to links and attachments. This includes links you receive on messaging apps and social media.
2. Download Apps and Media from Trusted Sources
It’s recommended to download apps and media from official websites such as Windows Store, Apple Store, and Google Play Store. However, if you do want to download something from an unknown website, please make sure that the website is safe.
3. Use an Ad Blocker
Malicious ads are infected ads, and if you click them, they will spread malware on your device. Malvertising also inserts malware into ad networks. Thus, you had better use an ad blocker to block them.
Related articles:
- 2021 Best 6 Free Adblock for Chrome | Block Ads on Chrome
- 2021 5 Best Free Ad Blockers for Edge – Block Ads in Edge
4. Turn on Firewall and Third-Party Antivirus
Install a firewall that can be used to detect any suspicious activity. Maybe, you are interested in this post –Windows Firewall for Windows 10 and Its Great Alternative. Besides, you can install, run, and regularly update anti-malware and anti-spyware software.
5. Keep the System Up-to-Date
No matter you are running Windows 10, Windows 8, or Windows 7, you should keep the system up-to-date. Microsoft always releases some security updates and patches to fix and prevent security leaks in the Windows system. Updating the system is helpful to keep the system secure.
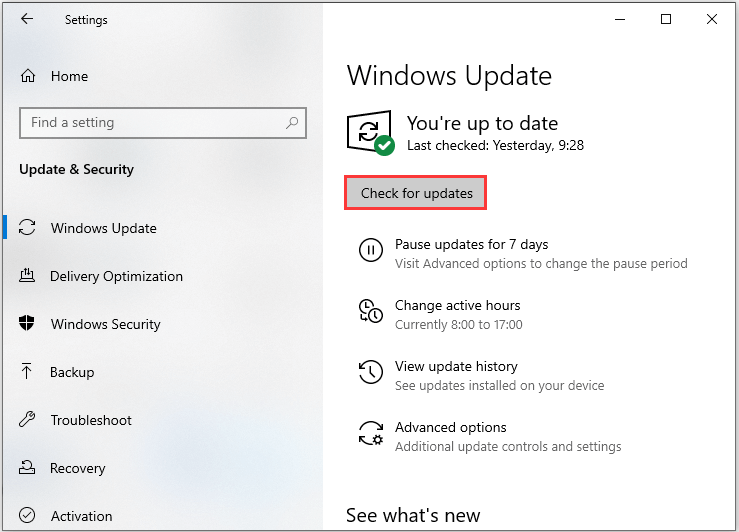
To do this work, go to Start > Settings > Update & Security in Windows 10 and click Check for update. Windows will check if there are available updates. If yes, it will download them and you need to restart the PC to finish the installation.
6. Back up Data Regularly
In many cases, if your computer is infected with a virus or worm, the data on your computer will be lost. Therefore, to keep your data safe, you need to back up your data in advance. You are highly recommended to use great backup software – MiniTool ShadowMaker.
MiniTool ShadowMaker is a powerful data protection and disaster recovery tool for your PC. With it, you can back up files, partitions, Windows operating system, and disks. You are also allowed to restore data if your system crashes, hard drive fails and more.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
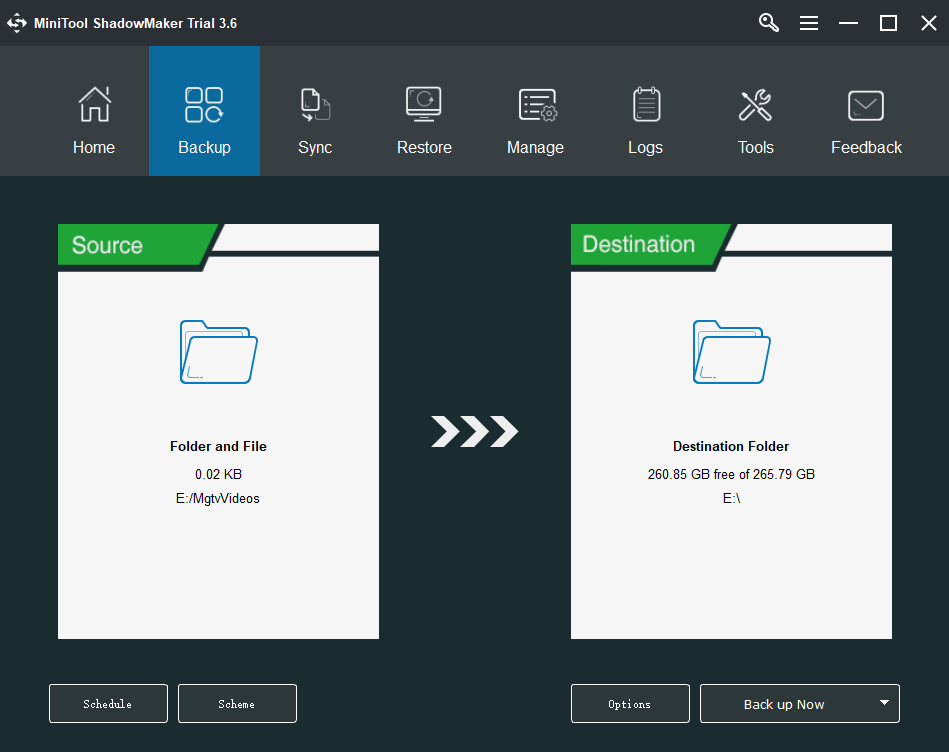
Step 1: Run MiniTool ShadowMaker Trial to its main interface.
Step 2: To back up files, go to Source > Folders and Files in the Backup tab, and choose the items you need. Then, you only need to choose the storage path.
Step 3: Click the Back up Now button to start the backup.
These six points are important things you should do to prevent the PC from the virus or worm.
Bottom Line
This post has briefly shown you some basic information about the virus vs worm and you can know how to avoid them. Besides, this post also introduces you to a powerful program – MiniTool ShadowMaker, which can help you back up data to protect it.
If you have any problems when you are using MiniTool software, please let us know. Or if you have any suggestions, also tell us. Sending an email to [email protected] or leaving a comment below is available.

User Comments :