What is a backdoor virus? How does a backdoor virus do? Most importantly, how to prevent its attack? In this article on MiniTool Website, all the problems above are answered in detail. If you are interested in it, follow up the guidelines in this article carefully.
What Is a Backdoor Virus?
A backdoor virus definition refers to a kind of malware that negates normal authentication procedures to access a system. It will create an alternative entry point into software, network or even a device that grants remote access to resources such as file servers and databases.
As soon as the entry point is created, hackers will scan the web for vulnerable programs and applications that they used to install backdoor viruses. After the backdoor viruses are installed on your device, it is very difficult to detect because their executable files are highly obfuscated.
The malicious activities of backdoor viruses usually contain:
- Surveillance
- Device hijacking
- Server hijacking
- Financial information theft
- Identity theft
- Distributed denial of service attacks (DDoS attacks)
- Advanced persistent threat assaults
- Watering hole attacks
- Website defacing
These activities are so harmful that they may impact negatively on your operating system and precious personal data. As a result, you are supposed to remain vigilant about the presence of backdoor viruses.
Types of Backdoor Viruses
There are many kinds of backdoor viruses and each of them has a different line of attack. In this part, I will introduce to you the 4 most common backdoor viruses.
Rootkits
Rootkit is a kind of advanced malware type which allows hackers to hide their activities and forces the system to grant root-level access. Once it is granted, hackers will be able to operate the system randomly such as modifying files, monitoring your activities, downloading malware and more.
What’s more, this type of backdoor virus can take the form of any used software or computer chips hence it is hard to detect them.
If you are interested in Rootkit and wonder how to remove it from your device, you can see this guide - How to Get Rid of Rootkit Windows 10? Here’re 4 Solutions for You.
Trojans
Like Rootkit, Trojan can also conceal its activities. It gets access to computers by fiddling with the verified file. Every time you download software, it will show a message: Allow insert-program-here to make changes on your device?
If you allow the permission, Trojans will be installed on the operating system and a backdoor is created. At last, hackers can do anything they want to do on your computer.
Hardware Backdoors
As the name suggests, hardware backdoors use hardware components such as CPUs, chips, and hard drives to break into a targeted system. Next, hackers and criminals will try to get root-level access to the system via these modified hardware components.
In addition to computer-related hardware, as long as the modified hardware parts are connected to a system, some other outside devices such as home security systems, phones, and thermostats can also perform as hardware backdoors.
Cryptographic Backdoors
You can compare a cryptographic backdoor to a master key which can unbolt all the content hidden behind the encrypted data. In such encryptions, both the communicating parties are granted a cryptographic key which is used to intercept and decrypt data. Cryptographic backdoors access important cryptographic keys and access your information without your knowledge.
Common System Flaws That Backdoor Can Exploit
Hackers can identify the weaknesses of the system and exploit them to install a backdoor virus. Here are the 4 most common system flaws:
Outdated Software
Outdated software is so vulnerable because it lacks some patches. Hackers will make use of it to install a backdoor on your device.
Weak Password
Simple and weak passwords can be easily cracked. Once hackers know your password, it is not difficult for them to install a backdoor virus on your device.
Open Network Ports
Hackers usually target open network ports because they can receive traffic from remote locations. They can take advantage of that to create a weak point and then it will be easy for them to install backdoor viruses.
A port scanner can help you to find and check all the programs running on the detected ports. If you are looking for reliable port scanners, see this guide - Top 5 Free Port Scanners for Windows 10.
Legitimate Backdoors
To get legitimate access for remote administration and troubleshooting, software or hardware developers need to leave a backdoor in their programs. Hackers may use the legitimate backdoor to attack the OS.
How to Prevent Backdoor Virus Attack?
# Fix 1: Update Your Software in Time
Outdated software is vulnerable and it can easily be exploited by cybercriminals to attack your device. Updating software to its latest version helps to fix these vulnerabilities. Therefore, it is advisable to update your apps and operating system regularly to reduce the risk of backdoor virus attacks.
# Fix 2: Change Your Password
To prevent unauthorized access, you had better create strong passwords that consist of capital & small letters, numbers and characters. If you don’t know how to create a unique password, you can rely on password managers.
It is also necessary to change your password at a regular basis. Try to enable Multi-Factor Authentication as much as you can. This method will help log out the hackers when they access the device the next time.
# Fix 3: Use Antivirus Software and Firewall
If you use reliable antivirus software and firewall, it is easy to detect and remove malware like backdoor viruses. Firewalls can also detect and prevent unwanted web traffic, that is to say, if the applications on your computer try to send data to an unknown network or someone outside your approved network tries to access your network, the firewall will stop the dangerous action.
Move 1: Open Windows Defender Firewall
If you notice that there is unknown web traffic or you doubt that you are infected by backdoor viruses, the first action is to block all your networks via Windows Defender Firewall.
It is of vital importance to keep your Windows Defender up to date. If you have no idea about how to update it, detailed instructions are given in this guide - How to Update Windows Defender Antivirus on Windows 10/11.
Step 1. Open Control Panel and scroll down to locate Windows Defender Firewall.
Step 2. In the left pane, hit Turn Windows Defender Firewall on or off.
Step 3. Tick Turn on Windows Defender Firewall both under Private network settings and Public network settings.
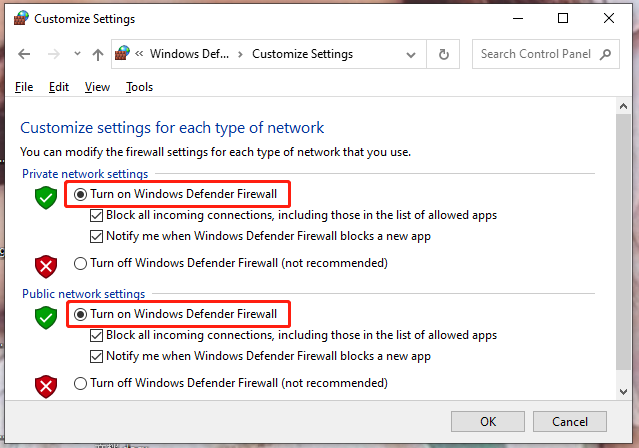
Don’t forget to tick the box beside Block all incoming connections, including those in the list of allowed apps.
Step 4. Press OK to save the changes.
What if you want to allow certain applications through Windows Defender Firewall? More detailed instructions are given in - How to Allow or Block a Program Through Firewall Windows 10.
Move 2: Run Windows Defender Offline Scan
Windows Defender can help you to get rid of backdoor viruses after blocking your network.
Step 1. Press the gear icon to open Windows Settings.
Step 2. In the settings menu, scroll down to look for Update & Security and tap on it.
Step 3. In the Windows Security tab, click on Virus & threat protection and choose Scan options under Current threats.
Step 4. Tick Microsoft Defender Offline scan and press Scan now.
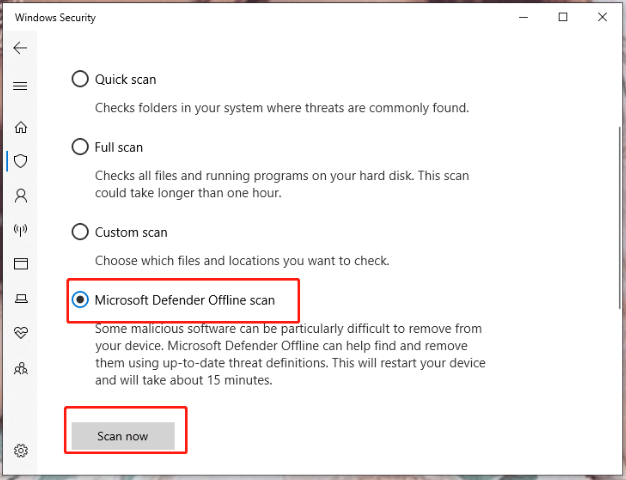
Step 5. After the scanning process is done, choose the backdoor virus files and delete them.
Do you know what the differences between antivirus software and firewall are? If you are curious about that, go to - Antivirus vs Firewall – How to Improve Your Data Security.
Suggestion: Back up Your Files Regularly
As mentioned in the beginning part, the backdoor virus attacks are so highly detrimental that they can harm your system. When your system is damaged, your important data may also be destroyed or missing.
If your computer is crashed and you don’t know what to do, please follow this guide to find potential fixes - Why Does My Computer Keeps Crashing? Here Are Answers and Fixes.
However, if you have backed up your computer and files, things would be easier. You can restore these files and restore your computer to a normal state in a few clicks.
How to back up your files? MiniTool ShadowMaker is a good option for that. It is a professional backup software which is designed to back up files, folders, partitions, disks and operating system. Now, let me show you how to create a file backup step by step.
Step 1. Download and install MiniTool ShadowMaker. You can enjoy its service for free within 30 days.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2. Launch the program and hit Keep Trial.
Step 3. Go to the Backup page and hit the Source button in the left pane.
Step 4. Choose Folders and Files and then tick the files that you want to back up.
Step 5. Hit OK to save it and hit the Destination button to select a destination path.
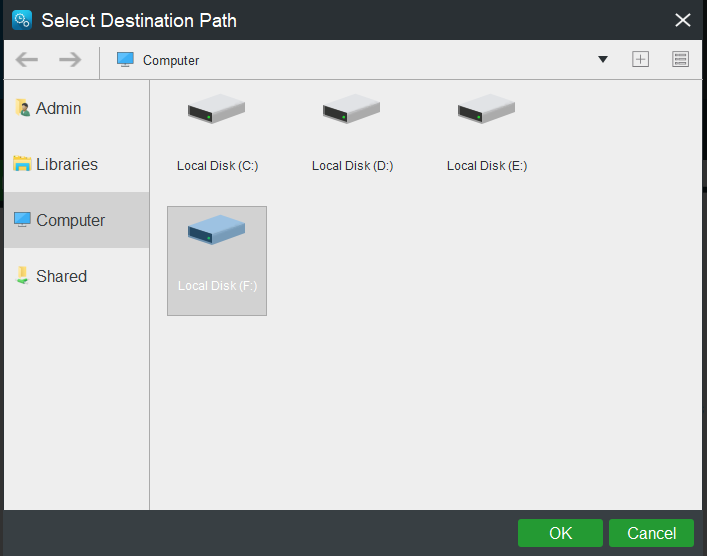
Step 5. Press Back up Now to start the process at once.
As for creating a system backup, you can go to this guide to get detailed guidelines - How to Back up Windows to Safeguard Your Computer? Try MiniTool.
Wrapping Things up
In conclusion, this article has shown what a backdoor virus is, how many types it has, common system flaws that it can exploit and how to prevent your operating system from it.
If you are also infected by backdoor viruses, the fixes mentioned above deserve a shot. At the same time, more suggestions about backdoor viruses and our products are also welcomed. You can send us emails via [email protected] or make a comment below.
Backdoor Virus FAQ
Backdoor virus is malware that can bypass all the implemented security measures and gain unauthorized access. Meanwhile, a backdoor virus can be legitimate itself. It is a hidden way of accessing an app, machine or network that can bypass basic security measures. Developers delete it before shipping products.
Poison Tap is one of the most notorious examples of backdoors. Once it is installed, hackers can gain root-level access to any website including those protected with 2FA.
In 2017, DoublePulsar was spotted with backdoor viruses. It allowed others to monitor Windows PCs. Cybercriminals can install powerful crucial cryptojacker featuring high memory to mine Bitcoin with the help of backdoor viruses.
Backdoor attack refers to that hackers exploit some vulnerabilities in your operating system such as easy passwords, outdated software, open network ports and more to get unauthorized permissions hence they can do what they want in your system.
Backdoor viruses can empower hackers greatly and allows them to do malicious activities like DDoS attacks, changing system settings, sending & receiving files and more. They can get root-level access and steal your data.




User Comments :